Difference between revisions of "Continuous Security Monitoring"
Tag: Manual revert |
|||
| (62 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
== Continuous Security Monitoring == | == Continuous Security Monitoring == | ||
Roadmap Creators: [https://www.linkedin.com/in/chelseaconard/| Chelsea Conard] and [https://www.linkedin.com/in/emlauber/| Em Lauber] | |||
Time Stamp: Dec 5, 2023 | |||
[[File:csm.png|300x300px]] | [[File:csm.png|300x300px]] | ||
| Line 7: | Line 10: | ||
=== Roadmap Overview === | === Roadmap Overview === | ||
A Continuous Security Monitoring (CSM) tool is critical to provide near-real-time surveillance and analysis of an environment to flag potential security threats. A CSM tool is an integral part of any modern cybersecurity framework. | A Continuous Security Monitoring (CSM) tool is critical to provide near-real-time surveillance and analysis of an environment to flag potential security threats. A CSM tool is an integral part of any modern cybersecurity framework. This technology is a Level 3. | ||
CSM technology affords automation as central to its operation, ensuring that the tool offers ongoing insights in the security posture of an environment and improves an organization's ability to manage potential risks. | |||
The technology functions with behavior analytics to monitor environmental activities in order to pinpoint potentially malicious or anomalous actions. The future of the technology includes advanced predicted analysis using Machine Learning (ML) and Artificial Intelligence (AI) tools where the tool can shift from reactive to proactive intelligence. In the long-term, quantum computing preparedness will be key to ensuring the tool can manage threats in a post-quantum computing world. The tool may also possess the ability to automatically repair itself, thought it currently operates in tandem with human intervention for optimal performance. | The technology functions with behavior analytics to monitor environmental activities in order to pinpoint potentially malicious or anomalous actions. The future of the technology includes advanced predicted analysis using Machine Learning (ML) and Artificial Intelligence (AI) tools where the tool can shift from reactive to proactive intelligence. In the long-term, quantum computing preparedness will be key to ensuring the tool can manage threats in a post-quantum computing world. The tool may also possess the ability to automatically repair itself, thought it currently operates in tandem with human intervention for optimal performance. | ||
| Line 46: | Line 51: | ||
[[File:Screen_Shot_2023-10-12_at_1.15.16_AM.png|500px]] | [[File:Screen_Shot_2023-10-12_at_1.15.16_AM.png|500px]] | ||
The FOM for Mean Time to Detect (MTTD) is plotted below as the evolution of the technology has afforded a decreased value for MTTD, approaching the theoretical limit of zero, or instantaneous detection. However, reaching an absolute zero MTTD may not be possible due to constraints such as processing time, network latency, and inherent limitation in detection algorithms. The sensitive nature of cybersecurity makes publicly available data a challenge, as well as data sharing. The novelty of the technology in the cybersecurity domain also contributes to the dearth of data and lack of historical data for the technology. Therefore, the resources listed in References informed the construction of the graph below. | The FOM for Mean Time to Detect (MTTD) is plotted below as the evolution of the technology has afforded a decreased value for MTTD, approaching the theoretical limit of zero, or instantaneous detection. However, reaching an absolute zero MTTD may not be possible due to constraints such as processing time, network latency, and inherent limitation in detection algorithms. The sensitive nature of cybersecurity makes publicly available data a challenge, as well as data sharing. The novelty of the technology in the cybersecurity domain also contributes to the dearth of data and lack of historical data for the technology. Therefore, 13 - 22 of the the resources listed in References informed the construction of the graph below. | ||
[[File:graph_overtime.png]] | [[File:graph_overtime.png]] | ||
=== Alignment with “Company” Strategic Drivers: FOM targets === | |||
=== Alignment with | |||
Through the lens of a hypothetical company, alignment with strategic drivers such as risk management, customer trust, operational efficiency, and scalability are all significant forces needed to ensure that the CSM tool would meet the market need and support the "company's" long-term objectives. | Through the lens of a hypothetical company, alignment with strategic drivers such as risk management, customer trust, operational efficiency, and scalability are all significant forces needed to ensure that the CSM tool would meet the market need and support the "company's" long-term objectives. | ||
| Line 63: | Line 67: | ||
'''Risk Management Alignment:''' | '''Risk Management Alignment:''' | ||
Target: Achieve industry-leading Mean Time to Detect (MTTD) for all categories of security threats | Target: Achieve industry-leading Mean Time to Detect (MTTD) for all categories of security threats by 2035 | ||
Action: Invest in analytics and threat intelligence to reduce MTTD, update threat databases, and improve algorithms for prediction | Action: Invest in analytics and threat intelligence to reduce MTTD, update threat databases, and improve algorithms for prediction | ||
Key Result: Aggregate and analyze the MTTD for the 5 biggest users our the CSM tool to identify industry-leading value | |||
'''Customer Trust Alignment:''' | '''Customer Trust Alignment:''' | ||
| Line 72: | Line 78: | ||
Action: Request feedback, offer transparent communication of security updates, and maintain best practices for incident response | Action: Request feedback, offer transparent communication of security updates, and maintain best practices for incident response | ||
Key Result: Analyze customer feedback to observe a pattern of high-values for trust scores | |||
'''Operational Efficiency Alignment:''' | '''Operational Efficiency Alignment:''' | ||
| Line 78: | Line 86: | ||
Action: Automate incident response and ensure integration with other operational tools to produce unified security | Action: Automate incident response and ensure integration with other operational tools to produce unified security | ||
Key Result: Aggregate and analyze the MTTR for the 5 biggest users our the CSM tool to identify industry-leading value | |||
'''Scalability Alignment:''' | '''Scalability Alignment:''' | ||
| Line 83: | Line 93: | ||
Target: Verify the CSM tool can support maximum endpoints on a network without performance degradation | Target: Verify the CSM tool can support maximum endpoints on a network without performance degradation | ||
Action: Design tool to interoperate with cloud environments, which can be | Action: Design tool to interoperate with cloud environments, which can be validated with stress testing | ||
Key Result: Confirm efficiency with expected performance time, also verifying pattern of successful stress testing | |||
'''Market Need Alignment:''' | '''Market Need Alignment:''' | ||
Target: Capture | Target: Capture 10% of the market within 6 months of launch | ||
Action: Conduct market research to compete on the product, utilize a competitive pricing strategy, and maintain active campaigns | Action: Conduct market research to compete on the product, utilize a competitive pricing strategy, and maintain active campaigns | ||
Key Result: Analyze return on investment of the marketing campaign through data from the Customer Relationship Management (CRM) tool | |||
'''Long-Term Objectives Support:''' | '''Long-Term Objectives Support:''' | ||
Target: Achieve sustainable growth to maintain a positive revenue stream | Target: Achieve sustainable growth to maintain a positive revenue stream by 2040 | ||
Action: Diversify the product's capabilities to keep up with emerging security threats and innovate with artificial intelligence to offer predictive capabilities | Action: Diversify the product's capabilities to keep up with emerging security threats and innovate with artificial intelligence to offer predictive capabilities | ||
Key Result: The comprehensive financial analysis conclusively demonstrates the sustained profitability of the company (including net profit margin, return on assets, earnings per share,cash flow, debt-to-equity ratio, etc.) | |||
=== Positioning of Company vs Competition: FOM charts === | === Positioning of Company vs Competition: FOM charts === | ||
| Line 115: | Line 131: | ||
Companies like CrowdStrike, with its Falcon tool, emphasize a security-centric portfolio, whereas Microsoft’s Defender is part of a broader software ecosystem. Observing the market through the lens of Gartner’s Magic Quadrant over time not only highlights the dynamic shifts in leadership positions, but also underscores the underlying technology strategies that have influenced these changes. Ultimately, the trend towards consolidation, seen in the acquisition of specialized startups by larger firms, suggests a movement towards coalescence in the market, reshaping the competitive landscape. | Companies like CrowdStrike, with its Falcon tool, emphasize a security-centric portfolio, whereas Microsoft’s Defender is part of a broader software ecosystem. Observing the market through the lens of Gartner’s Magic Quadrant over time not only highlights the dynamic shifts in leadership positions, but also underscores the underlying technology strategies that have influenced these changes. Ultimately, the trend towards consolidation, seen in the acquisition of specialized startups by larger firms, suggests a movement towards coalescence in the market, reshaping the competitive landscape. | ||
Our hypothetical "company" would compete more with CrowdStrike in its attempt to offer expertise solely in cybersecurity in order to produce the best CSM tool on the market, given that it's business model is more security-centric rather than a broad software ecosystem. | Our hypothetical "company" would compete more with CrowdStrike in its attempt to offer expertise solely in cybersecurity in order to produce the best CSM tool on the market, given that it's business model is more security-centric rather than a broad software ecosystem. We are targeting more of the Visionary quadrant by focusing on innovation in MTTD reduction. This choice in investment will limit our overall ability to be a leader since it can come at the expense of other investments in things like ecosystem support and sales pricing. At this point, we don't have the resources to compete with a large multi-offering player like Microsoft, but we can compete on being an expert in specialized security monitoring tools that go to the next generation of detection and response. Key to recognize from the Magic Quadrant is that a leader dominates in this industry only if it scores highest in the following criteria: Ability to Execute which includes Product/Service, Overall Viability, Sales Execution/Pricing, Market Responsiveness/Record, Marketing Execution, Customer Experience, and Operations plus Completeness of Vision which includes Marketing Understanding, Marketing Strategy, Sales Strategy, Offering (Product) Strategy, Business Model, Vertical/Industry Strategy, Innovation, and Geographic Strategy; thus, the "company" must compete with ingenuity, quality, and expertise to challenge CrowdStrike. | ||
=== Technical Model: Morphological Matrix & Tradespace === | === Technical Model: Morphological Matrix & Tradespace === | ||
| Line 122: | Line 138: | ||
[[File:Detect Time tornado chart.png|750x750px]] | [[File:Detect Time tornado chart.png|750x750px]] | ||
[[File:Normalized MTTD.png|750x750px]] | |||
While this can help us find theoretical optimizations within technical constraints limit, it does not consider business related impacts and decisions. For example, a high Efficiency of 10 would require a supercomputer and the average companies and CSM tools cannot afford that at this time. Likewise scanning every minute improves the Rate of scanning and thereby the Detection Time, but scanning every minute is not always feasible cost wise because scanning that much generates a lot of unnecessary data, slows performance overall of the system, and increases the cost since CSM tools sometimes cost by scan or network activity. Because of these business costs, customers must make judgment calls on their own risk to cost benefit of decreasing the Rate or increasing the Efficiency. | While this can help us find theoretical optimizations within technical constraints limit, it does not consider business related impacts and decisions. For example, a high Efficiency of 10 would require a supercomputer and the average companies and CSM tools cannot afford that at this time. Likewise scanning every minute improves the Rate of scanning and thereby the Detection Time, but scanning every minute is not always feasible cost wise because scanning that much generates a lot of unnecessary data, slows performance overall of the system, and increases the cost since CSM tools sometimes cost by scan or network activity. Because of these business costs, customers must make judgment calls on their own risk to cost benefit of decreasing the Rate or increasing the Efficiency. | ||
| Line 129: | Line 147: | ||
[[File:Coverage Tornado Chart.png|750x750px]] | [[File:Coverage Tornado Chart.png|750x750px]] | ||
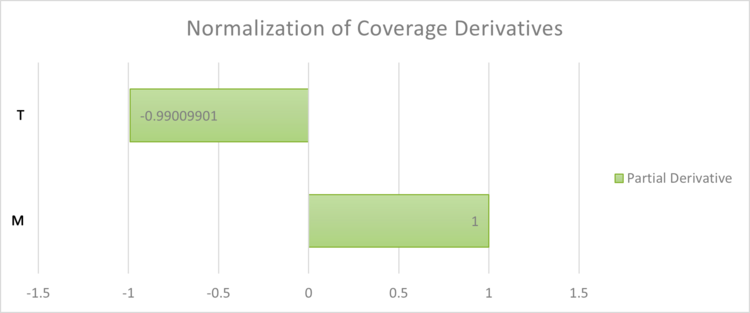
[[File:Normalized coverage.png|750x750px]] | |||
Similar to the Detection Time, the governing equations and optimizations for Coverage do not take into account the business impact of these inputs. For example, the least risky Coverage would be to have 100% of all activities within the system. This is not always feasible due to cost constraints or data processing, similar to the constraints on Number of Network Activities in Detection time. Companies may also define coverage differently whether they are accounting for coverage of open-source or third-party connections. Companies that use third-party tooling might assume that the tool company has complete coverage within their system, which is an assumption of risk. Customers need to make their own judgement call of cost to risk when determining the leverage of coverage required in their system. | Similar to the Detection Time, the governing equations and optimizations for Coverage do not take into account the business impact of these inputs. For example, the least risky Coverage would be to have 100% of all activities within the system. This is not always feasible due to cost constraints or data processing, similar to the constraints on Number of Network Activities in Detection time. Companies may also define coverage differently whether they are accounting for coverage of open-source or third-party connections. Companies that use third-party tooling might assume that the tool company has complete coverage within their system, which is an assumption of risk. Customers need to make their own judgement call of cost to risk when determining the leverage of coverage required in their system. | ||
| Line 134: | Line 154: | ||
=== Key Publications and Patents === | === Key Publications and Patents === | ||
{|class=wikitable | |||
!style="width: 50%;" | Patent | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
CN108449345B from China | |||
| style="vertical-align:top;" | | |||
The method specializes in the continuous safety monitoring of shadow assets on internet platforms. It conducts comparisons between the current state of shadow assets and historical data to emphasize the transition the assets undergo. The comparative analysis is instrumental to highlight potential differences between previously documented security threats and those that are actively monitored. Such insight is crucial to detect emerging vulnerabilities or breaches. | |||
|- | |||
| style="vertical-align:top;" | | |||
CN107493265B from Korea | |||
| style="vertical-align:top;" | | |||
The patent merges big data analytics and artificial intelligence (AI) to create a proactive defense mechanism against continuous cyber-attacks. The patent offers real-time response capability for a Continuous Security Monitoring (CSM) tool by allowing a system to not only be equipped to identify threats as they occur, but to also learn from incidents and better prepare for future attacks. Thus, the inclusion of AI creates an adaptive security posture, which is critical to the cybersecurity landscape in which threats evolve rapidly. The big data analytics also enhances the tool’s ability to process vast amounts of network data and identify patterns and anomalies that could signal an impending attack. The holistic view provided by AI can reduce the time to detect and respond, which can minimize potential damage from security incidents. | |||
|- | |||
| style="vertical-align:top;" | | |||
CN107493265B from China | |||
| style="vertical-align:top;" | | |||
The method monitors internally, performs a safety analysis, and generates associated safety management if abnormal behavior is found. | |||
|} | |||
CN107493265B follows CN108449345B in how they both afford real-time monitoring and analysis, yet the Korean patent adds the dimension of big data and AI to provide predictive security. CN107493265B is prioritized third because while ICS are crucial to cybersecurity, the area is niche. Nevertheless, the value in the patent lies in its potential to secure environments that are not only data-centric but also operationally critical, such as power grids, water treatment facilities, and manufacturing plants. The patent also builds on the two prior in that they all offer real-time monitoring capabilities, thus building off one another. Thus, the prioritization of the patents reflects a progression from general network asset monitoring to the integration of AI and big data for advanced threat detection and then to specialized applications for industrial control systems. Each step builds upon the foundation, reflecting how the technologies evolve from basic monitoring to sophisticated, predictive tools tailored to specific environments. | |||
{|class=wikitable | |||
!style="width: 50%;" | Publication | |||
!style="width: 50%;" | Purpose | |||
|- | |||
| style="vertical-align:top;" | | |||
“Leveraging Information Security Continuous Monitoring to Enhance Cybersecurity" | |||
| style="vertical-align:top;" | | |||
The work which exemplifies the role of CSM tools to establish data-driven risk management by offering near-real-time cyber situational awareness. The paper is aligned with our technology roadmap because of its recognition of the impact of CSM tools through its advocacy that federal government agencies adopt the technology. The authors highlight the tool’s ability to integrate massive amounts of diverse data from different sources and construct a comprehensive view of the agency’s security posture. | |||
|- | |||
| style="vertical-align:top;" | | |||
“APIRO, a Framework for Automated Security Tools API Recommendation” | |||
| style="vertical-align:top;" | | |||
The paper highlights how CSM tools can be integrated into Security Operation Centers (SOCs) to constantly scan, detect, and respond to cybersecurity threats. The authors recommend the most suitable APIs for integration to accelerate operational activities to ensure that a detected threat is addressed within a SOC. The paper is relevant to the scope of CSM tools because it encompasses the process of selecting and integrating the appropriate tools, which is a foundational step for effective continuous monitoring. | |||
|- | |||
| style="vertical-align:top;" | | |||
“Monitoring for Security Intrusion Using Performance Signatures” | |||
| style="vertical-align:top;" | | |||
The research introduces an innovative approach to detect security breaches by examining performance signatures, which are unique patterns indicative of a system’s operational state. The finding is that a deviation from the performance signature can be flagged as a potential security incident and would then be compared to known patterns of attack. The paper is more specialized in the detection phase of continuous monitoring. | |||
|} | |||
=== Financial Model === | === Financial Model === | ||
Assumptions: | |||
1) 30% YoY revenue growth | |||
2) Improving manufacturing margins due to improved learning curves/efficiencies | |||
3) 11% discount rate | |||
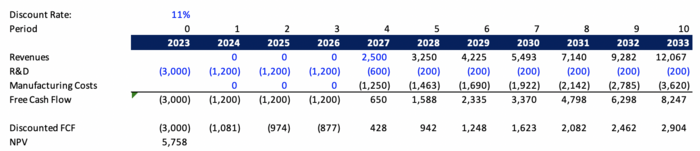
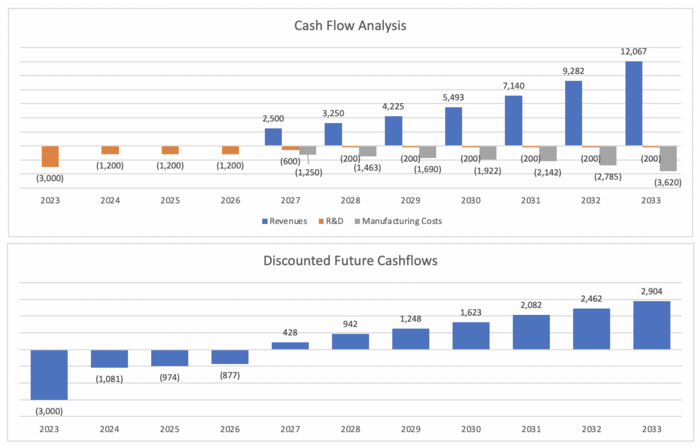
[[File:graph.png|700x700px]] | |||
Discounting the future cash flows at a discount rate of 11% yields a NPV of $5,758k. This also takes into consideration initial R&D investments of $3,000k in period 0 (2023). | |||
[[File:chart.png|700x700px]] | |||
Note: This analysis assumes the project ends in 2033 (i.e. no revenues passed this date). | |||
=== List of R&T Projects and Prototypes === | === List of R&T Projects and Prototypes === | ||
---------------------- | ---------------------- | ||
'''Open Source''' | '''Open Source''' | ||
---------------------- | ---------------------- | ||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:ossec.png|200x200px]] | |||
| style="vertical-align:top;" | | |||
OSSEC is an Open Source Host-based Intrusion Detection System that combines all aspects of HIDS (Host-based Intrusion Detection), log monitoring, and Security Incident Management (SIM)/Security Information and Event Management (SIEM) together in an open source solution. OSSEC allows customers to meet compliance requirements, including PCI and HIPAA. The solution is multi-platform, offers real-time and configurable alerts, and can be integrated with current infrastructure. | |||
|} | |||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:Wazuh.jpg|400x400px]] | [[File:Wazuh.jpg|400x400px]] | ||
| style="vertical-align:top;" | | |||
Wazuh is a fork of OSSEC, to unify separate functions into a single platform, offering endpoint and cloud workload protection.The core improvements Wazuh brings over OSSEC is to include endpoint protection, cloud workload protection, a unified security platform, and additional features and integration. | |||
|} | |||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:Elastic.png|200x200px]] | |||
| style="vertical-align:top;" | | |||
Elastic integrates Security Information and Event Management (SIEM) and endpoint security capabilities for threat hunting and detection. The technology allows an organization to more effectively monitor its endpoints and network, detect and respond to threats in real time, and proactively hunt for potential security breaches, all within a scalable framework. | |||
|} | |||
---------------------- | ---------------------- | ||
'''Commercial''' | '''Commercial''' | ||
---------------------- | ---------------------- | ||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:splunk.png|400x400px]] | [[File:splunk.png|400x400px]] | ||
Splunk provides continuous security monitoring through its Security Information and Event Management (SIEM) solution. | | style="vertical-align:top;" | | ||
Splunk provides continuous security monitoring through its Security Information and Event Management (SIEM) solution. The technology is widely recognized for its data analytic capabilities, aggregating vast amounts of data to identify potential security incidents. By analyzing logs, network traffic and user behaviors, Splunk can uncover hidden patterns and correlations that might suggest a security breach. Splunk also integrates with various threat intelligence feeds to cross-reference observed activities with known threat indicators. The technology also aids in incident response and forensic analysis by providing contextual information for forensic investigations. The data can assist organizations to maintain compliance with regulatory standards and visualize the outputs as reports and dashboards. | |||
|} | |||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:InsightIDR.png|400x400px]] | [[File:InsightIDR.png|400x400px]] | ||
InsightIDR is Rapid7's cloud-based solution for intrusion detection, behavioral analytics, and incident response capabilities. | | style="vertical-align:top;" | | ||
InsightIDR is Rapid7's cloud-based solution for intrusion detection, behavioral analytics, and incident response capabilities. InsightIDR excels in detecting intrusions by analyzing logs and by employing user behavior analytics (UBA) to establish normal activity patterns for users and entities within the network. By understanding typical behavior, InsightIDR can more accurately identify anomalies and reduce false positives. With its focus on user behavior, InsightIDR combines advanced analytics, threat intelligence, and automation to provide comprehensive visibility and enhance an organization's security posture. | |||
|} | |||
{|class=wikitable | |||
!style="width: 50%;" | Technology | |||
!style="width: 50%;" | Function | |||
|- | |||
| style="vertical-align:top;" | | |||
[[File:Falcon.png|400x400px]] | [[File:Falcon.png|400x400px]] | ||
| style="vertical-align:top;" | | |||
CrowdStrike Falcon is a prominent cloud-native endpoint protection platform (EPP). Being cloud-native, CrowdStrike Falcon leverages the cloud for high scalability and performance, offering rapid deployment and updates that provide real-time data analysis and threat detection. In the event of a detected threat, CrowdStrike Falcon facilitates immediate response. It provide tools for isolating affected endpoints, removes threats, and conducts a detailed investigation to capture the scope and impact of an attack. | |||
|} | |||
=== Technology Strategy Statement === | === Technology Strategy Statement === | ||
Our goal is to establish a state-of-the-art Continuous Security Monitoring Technology that offers near real-time surveillance of a digital infrastructure. The system is equipped to detect and respond to potential security threats, ensuring a robust security posture that minimizes risk, adheres to regulatory compliance, and offers comprehensive protections from a wide range of threats. | Our goal is to establish a state-of-the-art Continuous Security Monitoring (CSM) Technology that offers near real-time surveillance of a digital infrastructure. The system is equipped to detect and respond to potential security threats, ensuring a robust security posture that minimizes risk, adheres to regulatory compliance, and offers comprehensive protections from a wide range of threats. | ||
We will get there with advanced analytics, artificial intelligence, and machine learning techniques. These tools address the evolving landscape of cybersecurity challenges by boosting threat detection capabilities, improving response times, and maintaining a proactive approach to cybersecurity. | We will get there with advanced analytics, artificial intelligence, and machine learning techniques. These tools address the evolving landscape of cybersecurity challenges by boosting threat detection capabilities, improving response times, and maintaining a proactive approach to cybersecurity. | ||
We will invest | We will invest when we develop and refine our algorithms, maintain training programs to IT teams to leverage the technology, upgrade the digital infrastructures to support interoperability, and stay informed of best practices to incorporate into our strategy. | ||
[[File: | [[File:swoop.png|800x800px]] | ||
The Swoosh Chart above captures the initial stage of CSM technology to offer continuous security monitoring for endpoints. The next point highlights the rapid growth phase, where AI and ML are integrated into the technology to optimize performance and offer | The Swoosh Chart above captures the initial stage of CSM technology to offer continuous security monitoring for endpoints. The next point highlights the rapid growth phase, where AI and ML are integrated into the technology to optimize performance and offer near-real time detection and mitigation. In the stabilization phase, the technology is able to have the intelligence to have prediction capabilities. The evolution of the technology follows the NIST Cybersecurity Framework's pillars to detect, respond, and recover, and the technology has the future ability to predict, automating the remaining pillars identify and protect. The automation of the technology will allow prevention mechanisms that no human has thought of before. | ||
[[File:nist.png|400x400px]] | |||
=== References === | === References === | ||
[1] Cybersecurity Ventures. 2020. History of hacking and defenses. Retrieved from https://cybersecurityventures.com/the-history-of-cybercrime-and-cybersecurity-1940-2020/ | [1] Google Patents. 2018. Network asset continuous safety monitoring method, system, equipment and storage medium. Retrieved from [https://patents.google.com/patent/CN108449345B/en] | ||
[2] Google Patents. 2017. Information security network integrated management system using big data and artificial intelligence, and a method thereof. Retrieved from [https://patents.google.com/patent/KR101814368B1/en] | |||
[3] Google Patents. 2017. A kind of network security monitoring method towards industrial control system. Retrieved from [https://patents.google.com/patent/CN107493265B/en] | |||
[4] IEEE Xplore. 2021. Leveraging Information Security Continuous Monitoring to Enhance Cybersecurity. Retrieved from https://ieeexplore.ieee.org/document/9799002 | |||
[5] ACM Digital Library. 2023. APIRO: A Framework for Automated Security Tools API Recommendation. Retrieved from https://dl-acm-org.libproxy.mit.edu/doi/10.1145/3512768 | |||
[6] ACM Digital Library. 2010. Monitoring for security intrusion using performance signatures. Retrieved from https://dl-acm-org.libproxy.mit.edu/doi/10.1145/1712605.1712623 | |||
[7] OSSEC. 2021. Getting started with OSSEC. Retrieved from https://www.ossec.net/docs/docs/manual/non-technical-overview.html | |||
[8] Wazuh. 2023. The open source security platform. Retrieved from https://wazuh.com/ | |||
[9] Gartner. 2023. Elastic Security Reviews. Retrieved from https://www.gartner.com/reviews/market/endpoint-protection-platforms/vendor/elasticsearch/product/elastic-security | |||
[10] Splunk. 2023. Splunk Enterprise Security. Retrieved from https://www.splunk.com/en_us/products/enterprise-security.html | |||
[11] Rapid 7. 2023. Security information and event management. Retrieved from https://www.rapid7.com/products/insightidr/features/security-information-event-management/ | |||
[12]Crowdstrike. 2023. Falcon: The world’s leading AI-native platform for unified next-gen antivirus. Retrieved from https://www.crowdstrike.com/products/endpoint-security/falcon-prevent-antivirus/ | |||
[13] Cybersecurity Ventures. 2020. History of hacking and defenses. Retrieved from https://cybersecurityventures.com/the-history-of-cybercrime-and-cybersecurity-1940-2020/ | |||
[14] Statista. 2023. Median time from compromise to discovery in days of larger organizations worldwide from 2014 to 2019. Retrieved from https://www.statista.com/statistics/221406/time-between-initial-compromise-and-discovery-of-larger-organizations/ | |||
[15] Gartner. 2023. List of Critical Capabilities for Cloud Access Security Brokers. Retrieved from https://www.gartner.com/document/4366499 | |||
[16] Oberheide, J., & Cooke, E. 2008. CloudAV: N-Version Antivirus in the Network Cloud. Retrieved from https://www.semanticscholar.org/paper/CloudAV%3A-N-Version-Antivirus-in-the-Network-Cloud-Oberheide-Cooke/1ca0b25bd4fe4994f7f5e334987588776a1a123c | |||
[ | [17] Secureworks. 2017. The Evolution of Intrusion Detection & Prevention. Retrieved from https://www.secureworks.com/blog/the-evolution-of-intrusion-detection-prevention | ||
[ | [18] ISACA. 2021. The Evolution of Security Operations and Strategies for Building an Effective SOC. ISACA Journal, 5. Retrieved from https://www.isaca.org/resources/isaca-journal/issues/2021/volume-5/the-evolution-of-security-operations-and-strategies-for-building-an-effective-soc | ||
[ | [19] Pure Storage. 2023. What is SOAR? Retrieved from https://www.purestorage.com/knowledge/what-is-soar.html | ||
[ | [20] Brand Essence Research. 2023. Security Orchestration, Automation and Response Market. Retrieved from https://brandessenceresearch.com/security/security-orchestration-automation-and-response-market | ||
[ | [21] CrowdStrike. 2023. Falcon Insight XDR. Retrieved from https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/ | ||
[ | [22] CrowdStrike. 2023. CrowdStrike Announces General Availability of Falcon XDR. Retrieved from https://www.crowdstrike.com/press-releases/crowdstrike-announces-general-availability-of-falcon-xdr/ | ||
[ | [23] National Institute of Standards and Technology. 2023. Cybersecurity Framework. Retrieved from https://www.nist.gov/cyberframework | ||
[ | [[Healthcare_Data_Security]] | ||
Latest revision as of 03:30, 3 February 2024
Continuous Security Monitoring
Roadmap Creators: Chelsea Conard and Em Lauber
Time Stamp: Dec 5, 2023
Roadmap Overview
A Continuous Security Monitoring (CSM) tool is critical to provide near-real-time surveillance and analysis of an environment to flag potential security threats. A CSM tool is an integral part of any modern cybersecurity framework. This technology is a Level 3.
CSM technology affords automation as central to its operation, ensuring that the tool offers ongoing insights in the security posture of an environment and improves an organization's ability to manage potential risks.
The technology functions with behavior analytics to monitor environmental activities in order to pinpoint potentially malicious or anomalous actions. The future of the technology includes advanced predicted analysis using Machine Learning (ML) and Artificial Intelligence (AI) tools where the tool can shift from reactive to proactive intelligence. In the long-term, quantum computing preparedness will be key to ensuring the tool can manage threats in a post-quantum computing world. The tool may also possess the ability to automatically repair itself, thought it currently operates in tandem with human intervention for optimal performance.
Further, the increasing regulation of cyber space and introduction of cybersecurity policy suggest the CSM tool may also be a requirement for regulatory compliance and would allow environments to stay updated with evolving cybersecurity laws and regulations.
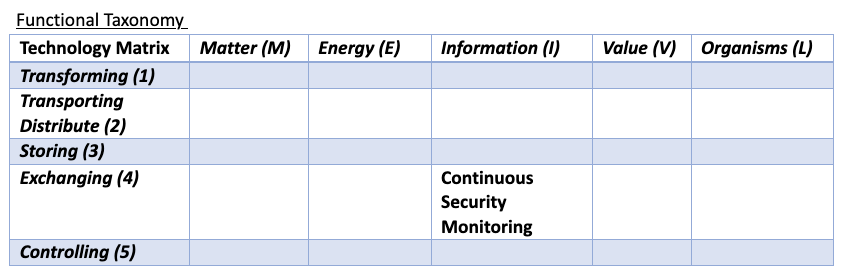
The visual below offers insight on where the CSM tool exists in the 5x5 matrix:
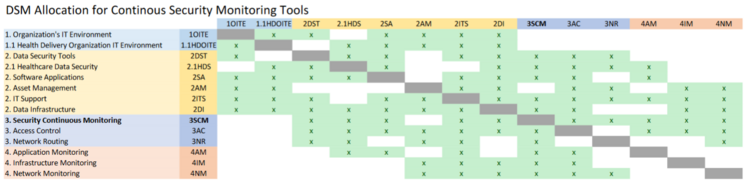
DSM Allocation
The most inter-dependencies are with the Healthcare Data Security (2HDS) roadmap. The Healthcare Data Security roadmap is narrowed in to a specific industry whereas we are focused on the more generalized industrial application but a deeper technical level of data security, Continuous Security Monitoring. The higher levels are essentially the same across roadmaps, but industry specific vs generalized. As such, we’ve marked the Healthcare specific roadmap items as subcategories underneath the non-industry specific version. We decided to omit the industry specific items, such as Medical Device Protection, from our DSM.
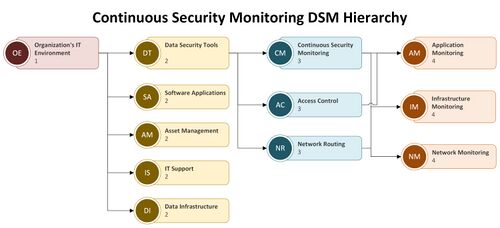
A more detailed view of the levels for the roadmap interactions is provided in hierarchy form.
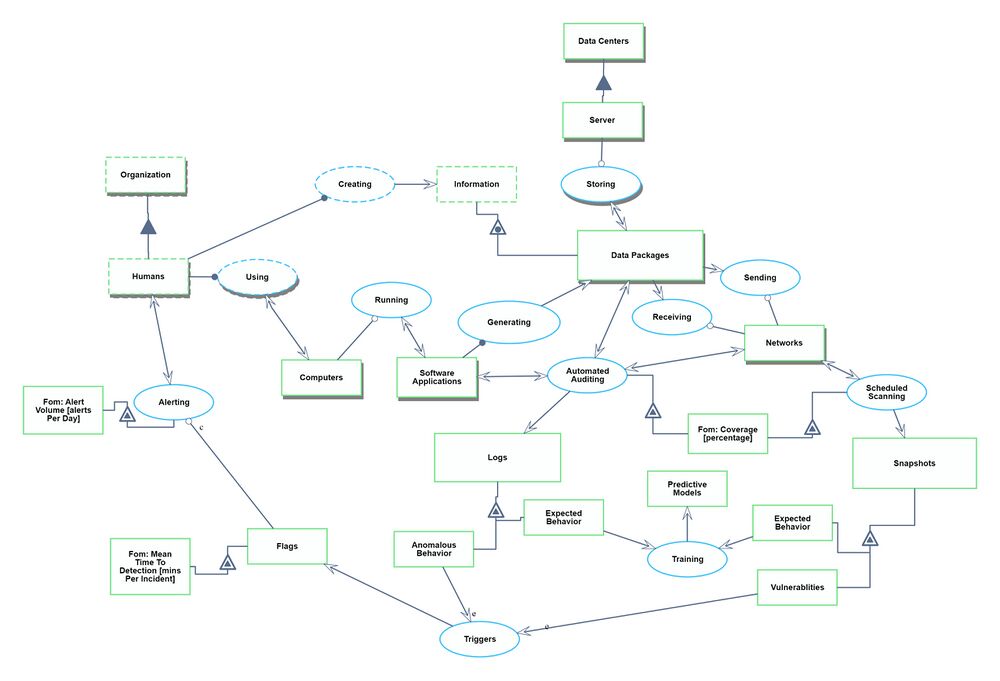
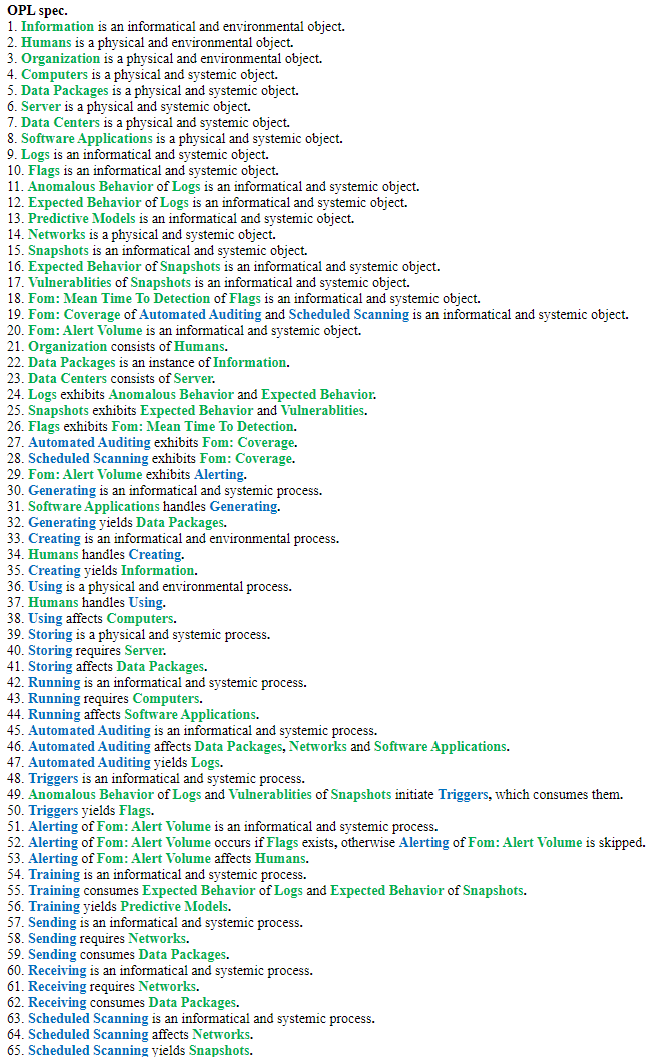
Roadmap Model using OPM (ISO 19450)
We defined a Continuous Security Monitoring (CSM) tool to sit within the environment of an organization's Information Technology (IT) infrastructure. The system contains the IT landscape at a high level, such as software applications, data infrastructure, and network routing. We narrowed to just the monitoring and alerting functionality of a CSM tool. There could be additional functionalities within data security such as root cause analysis, remediation, and pro-active repairs, but we have excluded those from our system.
Note: Automated Auditing refers to the automatic generation of logs and monitoring of networks and applications to ensure compliance with security policies and standards.
The Object-Process Model above can be written in natural language as follows:
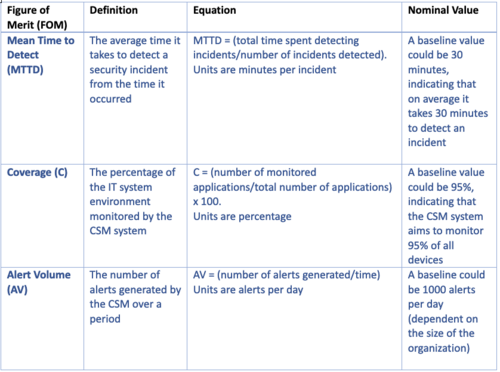
Figures of Merit (FOM): Definition (name, unit, trends dFOM/dt)
The table below delineates three critical Figures of Merit (FOM) for a CSM tool, in order of priority:
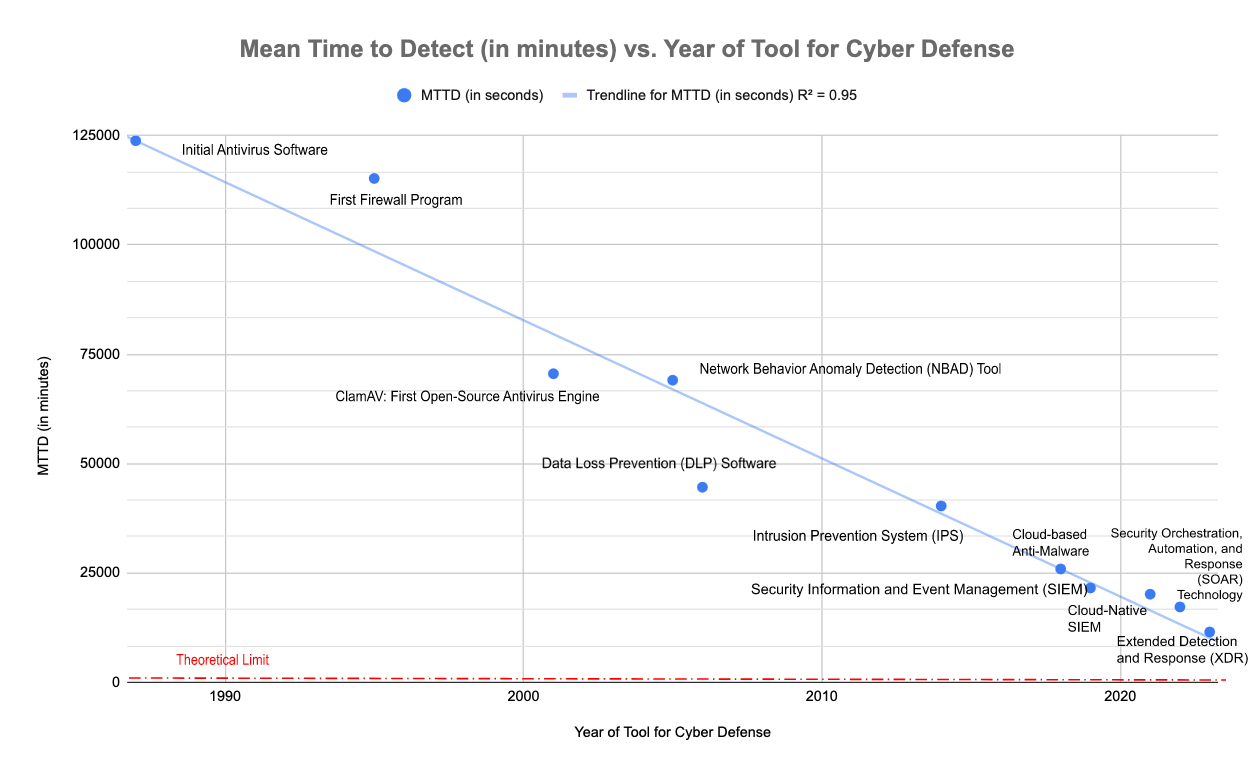
The FOM for Mean Time to Detect (MTTD) is plotted below as the evolution of the technology has afforded a decreased value for MTTD, approaching the theoretical limit of zero, or instantaneous detection. However, reaching an absolute zero MTTD may not be possible due to constraints such as processing time, network latency, and inherent limitation in detection algorithms. The sensitive nature of cybersecurity makes publicly available data a challenge, as well as data sharing. The novelty of the technology in the cybersecurity domain also contributes to the dearth of data and lack of historical data for the technology. Therefore, 13 - 22 of the the resources listed in References informed the construction of the graph below.
Alignment with “Company” Strategic Drivers: FOM targets
Through the lens of a hypothetical company, alignment with strategic drivers such as risk management, customer trust, operational efficiency, and scalability are all significant forces needed to ensure that the CSM tool would meet the market need and support the "company's" long-term objectives.
Assessing risk management and operational efficiency is captured in Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). The company would want a tool with the least value for MTTD to detect anomalous behavior as fast as competitors' tools in the marketplace. Similarly, the best tool on the market would also offer the smallest MTTR. Further, a CSM tool with the least MTTD would reign as a top product on the market and create customer trust.
Meanwhile, to ensure scalability of the tool, the company will want clients to implement the CSM tool throughout their networks. Dependency is a powerful form of equity and clients who integrate the tool to the maximum-level possible of coverage for their networks will rely on the tool in the present and future.
In summary:
Risk Management Alignment:
Target: Achieve industry-leading Mean Time to Detect (MTTD) for all categories of security threats by 2035
Action: Invest in analytics and threat intelligence to reduce MTTD, update threat databases, and improve algorithms for prediction
Key Result: Aggregate and analyze the MTTD for the 5 biggest users our the CSM tool to identify industry-leading value
Customer Trust Alignment:
Target: Establish a trust score that is above industry average
Action: Request feedback, offer transparent communication of security updates, and maintain best practices for incident response
Key Result: Analyze customer feedback to observe a pattern of high-values for trust scores
Operational Efficiency Alignment:
Target: Reduce Mean Team to Respond (MTTR) to incidents
Action: Automate incident response and ensure integration with other operational tools to produce unified security
Key Result: Aggregate and analyze the MTTR for the 5 biggest users our the CSM tool to identify industry-leading value
Scalability Alignment:
Target: Verify the CSM tool can support maximum endpoints on a network without performance degradation
Action: Design tool to interoperate with cloud environments, which can be validated with stress testing
Key Result: Confirm efficiency with expected performance time, also verifying pattern of successful stress testing
Market Need Alignment:
Target: Capture 10% of the market within 6 months of launch
Action: Conduct market research to compete on the product, utilize a competitive pricing strategy, and maintain active campaigns
Key Result: Analyze return on investment of the marketing campaign through data from the Customer Relationship Management (CRM) tool
Long-Term Objectives Support:
Target: Achieve sustainable growth to maintain a positive revenue stream by 2040
Action: Diversify the product's capabilities to keep up with emerging security threats and innovate with artificial intelligence to offer predictive capabilities
Key Result: The comprehensive financial analysis conclusively demonstrates the sustained profitability of the company (including net profit margin, return on assets, earnings per share,cash flow, debt-to-equity ratio, etc.)
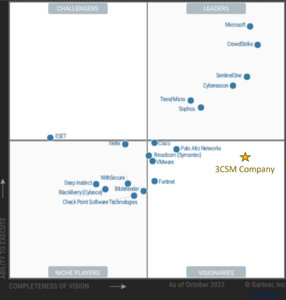
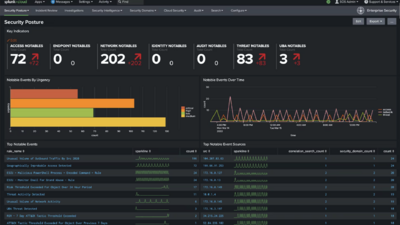
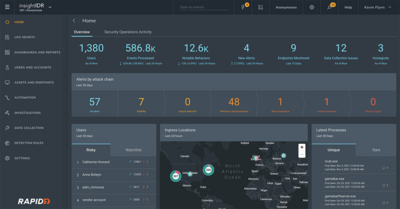
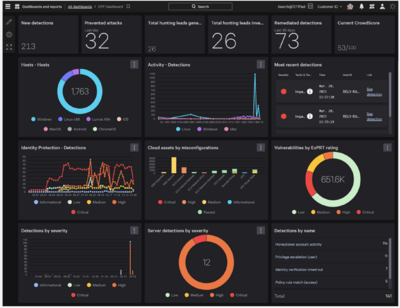
Positioning of Company vs Competition: FOM charts
The Continuous Security Monitoring (CSM) market is notably saturated with a plethora of one-off tools and emerging startups, each offering varied monitoring solutions. To refine our analysis, we will zero in on detection and our "company" will offer a tool for endpoint detection for continuous security monitoring. The CSM tool is critical to monitor end-user devices like desktops, laptops, and mobile devices from malicious activity.
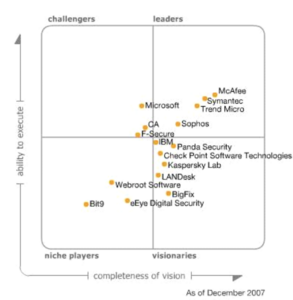
In evaluating the competitive landscape of the CSM tool, we will focus on the Mean Time to Detect (MTTD) as a primary Figure of Merit (FOM) in our roadmap. However, given the challenges associated with collecting comparable MTTD data across various companies, due to the high dependency of MTTD on the specific environment and setup, we will pivot to utilizing Gartner’s Magic Quadrant analysis of Endpoint Protection tools. The Magic Quadrant uses criteria of Ability to Execute which includes Product/Service, Overall Viability, Sales Execution/Pricing, Market Responsiveness/Record, Marketing Execution, Customer Experience, and Operations plus Completeness of Vision which includes Marketing Understanding, Marketing Strategy, Sales Strategy, Offering (Product) Strategy, Business Model, Vertical/Industry Strategy, Innovation, and Geographic Strategy.
The above left is the the Magic Quadrants for Endpoint Protection Platforms in 2007. The right is the Magic Quadrant for endpoint protection platforms as of October 2022. The Magic Quadrant shows 18 providers placed in either the Leaders, Challengers, Visionaries or Niche Players. Providers are positioned based on ability to execute and completeness of vision.
An examination of the evolution within the Magic Quadrant from 2007 to 2022 reveals significant shifts. Initially, in 2007, Microsoft was positioned as a challenger but has ascended to the top leader spot in 2022. In contrast, CrowdStrike, another top leader in 2022, was not even listed in 2007. This raises the question of the strategic moves over those 15 years that have redefined the market standards.
Microsoft leveraged its existing market presence by integrating Network Access Protection into its widely used Windows operating system, synergizing endpoint protection with its suite of enterprise and consumer products. Microsoft’s strategy, coupled with the pervasive use of its platforms for essential services, facilitated the seamless adoption of its endpoint protection solutions.
CrowdStrike, on the other hand, has carved out its leadership through a dedicated focus on cybersecurity. As a specialized entity, it has been able to channel deep industry knowledge into the development of robust security products tailored to specific security needs. This focus has allowed it to distinguish itself and create products that resonate with the evolving demands of cybersecurity. The endpoint protection market itself has evolved from a collection of disparate software applications, such as antivirus programs, to more integrated solutions. Major platforms now commonly offer these protections as built-in features, both for consumer security and in tiered services for enterprise clients. The pricing strategies in this market vary, with some providers offering a flat fee up to a certain usage level followed by activity-based pricing, while others charged based on the scale of usage – such as the number of applications monitored, users, or endpoints.
Companies like CrowdStrike, with its Falcon tool, emphasize a security-centric portfolio, whereas Microsoft’s Defender is part of a broader software ecosystem. Observing the market through the lens of Gartner’s Magic Quadrant over time not only highlights the dynamic shifts in leadership positions, but also underscores the underlying technology strategies that have influenced these changes. Ultimately, the trend towards consolidation, seen in the acquisition of specialized startups by larger firms, suggests a movement towards coalescence in the market, reshaping the competitive landscape.
Our hypothetical "company" would compete more with CrowdStrike in its attempt to offer expertise solely in cybersecurity in order to produce the best CSM tool on the market, given that it's business model is more security-centric rather than a broad software ecosystem. We are targeting more of the Visionary quadrant by focusing on innovation in MTTD reduction. This choice in investment will limit our overall ability to be a leader since it can come at the expense of other investments in things like ecosystem support and sales pricing. At this point, we don't have the resources to compete with a large multi-offering player like Microsoft, but we can compete on being an expert in specialized security monitoring tools that go to the next generation of detection and response. Key to recognize from the Magic Quadrant is that a leader dominates in this industry only if it scores highest in the following criteria: Ability to Execute which includes Product/Service, Overall Viability, Sales Execution/Pricing, Market Responsiveness/Record, Marketing Execution, Customer Experience, and Operations plus Completeness of Vision which includes Marketing Understanding, Marketing Strategy, Sales Strategy, Offering (Product) Strategy, Business Model, Vertical/Industry Strategy, Innovation, and Geographic Strategy; thus, the "company" must compete with ingenuity, quality, and expertise to challenge CrowdStrike.
Technical Model: Morphological Matrix & Tradespace
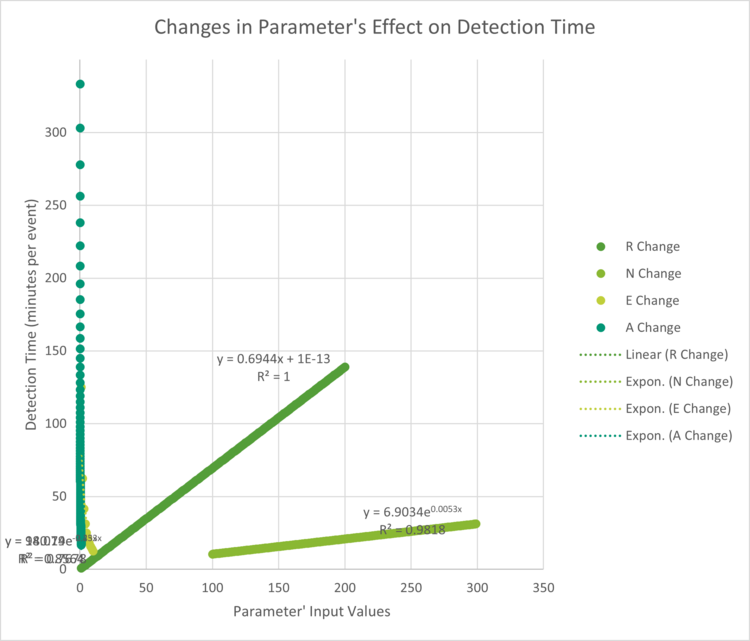
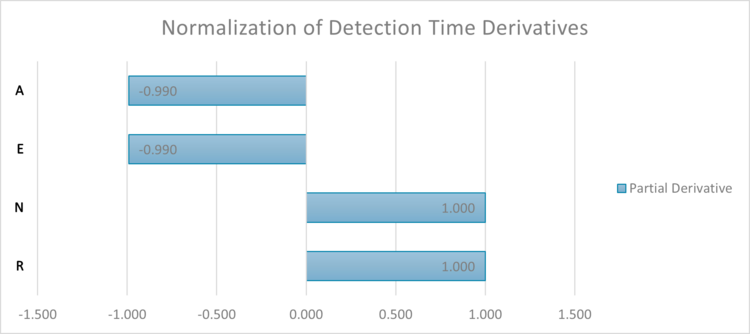
Of the variables in MTTD, only Incident Detect Time (also called Detection Time) is within a tooling’s control. The Number of Incidents and Incident Start Time is more often determined by external factors. For a baseline design, say we have an Incident that starts on one of our endpoints. Our tool scans every 30 minutes (R). Each scan has 600 network events (N). The efficiency (E) of data processing is the ability of the tool to quickly analyze those total network events to only the relevant ones. Efficiency is rated on a scale of 1-10 where 1 is the least efficient such as a human manually reviewing the network events for processing and 10 is the most efficient using a supercomputer for data processing. Our baseline design has an efficiency coefficient of 6, which equates to a modern cloud processing engine but it is not fully optimized. Accuracy (A) is the measurement of how likely the identified relevant events are true security incidents vs false negatives or false positives. Our baseline design has an 80% accuracy. For the baseline design, what is the likely time passed from incident start until detection (IDetect)? 62.5 minutes per event. Changes in the parameters and their effect on Detection Time is below.
While this can help us find theoretical optimizations within technical constraints limit, it does not consider business related impacts and decisions. For example, a high Efficiency of 10 would require a supercomputer and the average companies and CSM tools cannot afford that at this time. Likewise scanning every minute improves the Rate of scanning and thereby the Detection Time, but scanning every minute is not always feasible cost wise because scanning that much generates a lot of unnecessary data, slows performance overall of the system, and increases the cost since CSM tools sometimes cost by scan or network activity. Because of these business costs, customers must make judgment calls on their own risk to cost benefit of decreasing the Rate or increasing the Efficiency. The Detection Time can also only be on parts of the customer’s system that is monitored. Coverage is an FOM that measures the percentage of the network system that is monitored by a tool vs total activities within the system.
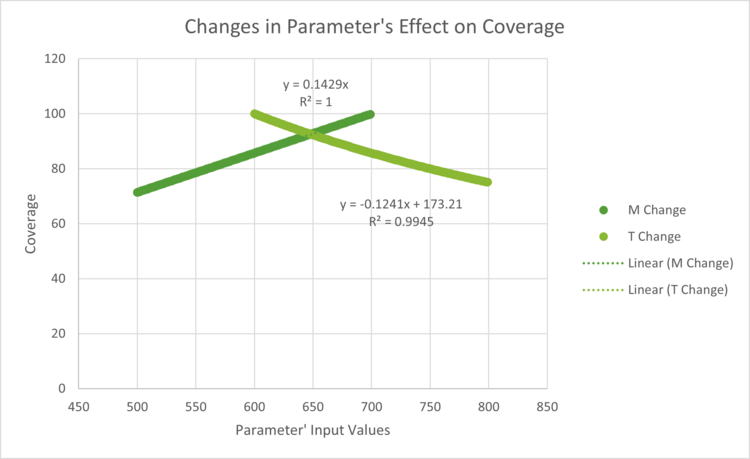
If we extend the baseline design from the MTTD, the 600 events for N for Number of network activities becomes the Monitored Activities in the Coverage governing equation. We will assume a baseline design where Total Activities in the System is 700. This design has a coverage of 85.7%.
Similar to the Detection Time, the governing equations and optimizations for Coverage do not take into account the business impact of these inputs. For example, the least risky Coverage would be to have 100% of all activities within the system. This is not always feasible due to cost constraints or data processing, similar to the constraints on Number of Network Activities in Detection time. Companies may also define coverage differently whether they are accounting for coverage of open-source or third-party connections. Companies that use third-party tooling might assume that the tool company has complete coverage within their system, which is an assumption of risk. Customers need to make their own judgement call of cost to risk when determining the leverage of coverage required in their system.
Key Publications and Patents
| Patent | Function |
|---|---|
|
CN108449345B from China |
The method specializes in the continuous safety monitoring of shadow assets on internet platforms. It conducts comparisons between the current state of shadow assets and historical data to emphasize the transition the assets undergo. The comparative analysis is instrumental to highlight potential differences between previously documented security threats and those that are actively monitored. Such insight is crucial to detect emerging vulnerabilities or breaches. |
|
CN107493265B from Korea |
The patent merges big data analytics and artificial intelligence (AI) to create a proactive defense mechanism against continuous cyber-attacks. The patent offers real-time response capability for a Continuous Security Monitoring (CSM) tool by allowing a system to not only be equipped to identify threats as they occur, but to also learn from incidents and better prepare for future attacks. Thus, the inclusion of AI creates an adaptive security posture, which is critical to the cybersecurity landscape in which threats evolve rapidly. The big data analytics also enhances the tool’s ability to process vast amounts of network data and identify patterns and anomalies that could signal an impending attack. The holistic view provided by AI can reduce the time to detect and respond, which can minimize potential damage from security incidents. |
|
CN107493265B from China |
The method monitors internally, performs a safety analysis, and generates associated safety management if abnormal behavior is found. |
CN107493265B follows CN108449345B in how they both afford real-time monitoring and analysis, yet the Korean patent adds the dimension of big data and AI to provide predictive security. CN107493265B is prioritized third because while ICS are crucial to cybersecurity, the area is niche. Nevertheless, the value in the patent lies in its potential to secure environments that are not only data-centric but also operationally critical, such as power grids, water treatment facilities, and manufacturing plants. The patent also builds on the two prior in that they all offer real-time monitoring capabilities, thus building off one another. Thus, the prioritization of the patents reflects a progression from general network asset monitoring to the integration of AI and big data for advanced threat detection and then to specialized applications for industrial control systems. Each step builds upon the foundation, reflecting how the technologies evolve from basic monitoring to sophisticated, predictive tools tailored to specific environments.
| Publication | Purpose |
|---|---|
|
“Leveraging Information Security Continuous Monitoring to Enhance Cybersecurity" |
The work which exemplifies the role of CSM tools to establish data-driven risk management by offering near-real-time cyber situational awareness. The paper is aligned with our technology roadmap because of its recognition of the impact of CSM tools through its advocacy that federal government agencies adopt the technology. The authors highlight the tool’s ability to integrate massive amounts of diverse data from different sources and construct a comprehensive view of the agency’s security posture. |
|
“APIRO, a Framework for Automated Security Tools API Recommendation” |
The paper highlights how CSM tools can be integrated into Security Operation Centers (SOCs) to constantly scan, detect, and respond to cybersecurity threats. The authors recommend the most suitable APIs for integration to accelerate operational activities to ensure that a detected threat is addressed within a SOC. The paper is relevant to the scope of CSM tools because it encompasses the process of selecting and integrating the appropriate tools, which is a foundational step for effective continuous monitoring. |
|
“Monitoring for Security Intrusion Using Performance Signatures” |
The research introduces an innovative approach to detect security breaches by examining performance signatures, which are unique patterns indicative of a system’s operational state. The finding is that a deviation from the performance signature can be flagged as a potential security incident and would then be compared to known patterns of attack. The paper is more specialized in the detection phase of continuous monitoring. |
Financial Model
Assumptions:
1) 30% YoY revenue growth 2) Improving manufacturing margins due to improved learning curves/efficiencies 3) 11% discount rate
Discounting the future cash flows at a discount rate of 11% yields a NPV of $5,758k. This also takes into consideration initial R&D investments of $3,000k in period 0 (2023).
Note: This analysis assumes the project ends in 2033 (i.e. no revenues passed this date).
List of R&T Projects and Prototypes
Open Source
| Technology | Function |
|---|---|
|
OSSEC is an Open Source Host-based Intrusion Detection System that combines all aspects of HIDS (Host-based Intrusion Detection), log monitoring, and Security Incident Management (SIM)/Security Information and Event Management (SIEM) together in an open source solution. OSSEC allows customers to meet compliance requirements, including PCI and HIPAA. The solution is multi-platform, offers real-time and configurable alerts, and can be integrated with current infrastructure. |
| Technology | Function |
|---|---|
|
Wazuh is a fork of OSSEC, to unify separate functions into a single platform, offering endpoint and cloud workload protection.The core improvements Wazuh brings over OSSEC is to include endpoint protection, cloud workload protection, a unified security platform, and additional features and integration. |
| Technology | Function |
|---|---|
|
Elastic integrates Security Information and Event Management (SIEM) and endpoint security capabilities for threat hunting and detection. The technology allows an organization to more effectively monitor its endpoints and network, detect and respond to threats in real time, and proactively hunt for potential security breaches, all within a scalable framework. |
Commercial
| Technology | Function |
|---|---|
|
Splunk provides continuous security monitoring through its Security Information and Event Management (SIEM) solution. The technology is widely recognized for its data analytic capabilities, aggregating vast amounts of data to identify potential security incidents. By analyzing logs, network traffic and user behaviors, Splunk can uncover hidden patterns and correlations that might suggest a security breach. Splunk also integrates with various threat intelligence feeds to cross-reference observed activities with known threat indicators. The technology also aids in incident response and forensic analysis by providing contextual information for forensic investigations. The data can assist organizations to maintain compliance with regulatory standards and visualize the outputs as reports and dashboards. |
| Technology | Function |
|---|---|
|
InsightIDR is Rapid7's cloud-based solution for intrusion detection, behavioral analytics, and incident response capabilities. InsightIDR excels in detecting intrusions by analyzing logs and by employing user behavior analytics (UBA) to establish normal activity patterns for users and entities within the network. By understanding typical behavior, InsightIDR can more accurately identify anomalies and reduce false positives. With its focus on user behavior, InsightIDR combines advanced analytics, threat intelligence, and automation to provide comprehensive visibility and enhance an organization's security posture. |
| Technology | Function |
|---|---|
|
CrowdStrike Falcon is a prominent cloud-native endpoint protection platform (EPP). Being cloud-native, CrowdStrike Falcon leverages the cloud for high scalability and performance, offering rapid deployment and updates that provide real-time data analysis and threat detection. In the event of a detected threat, CrowdStrike Falcon facilitates immediate response. It provide tools for isolating affected endpoints, removes threats, and conducts a detailed investigation to capture the scope and impact of an attack. |
Technology Strategy Statement
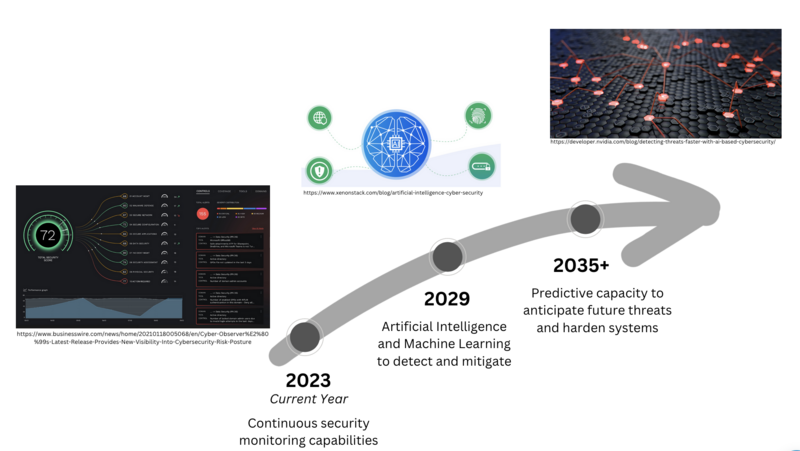
Our goal is to establish a state-of-the-art Continuous Security Monitoring (CSM) Technology that offers near real-time surveillance of a digital infrastructure. The system is equipped to detect and respond to potential security threats, ensuring a robust security posture that minimizes risk, adheres to regulatory compliance, and offers comprehensive protections from a wide range of threats.
We will get there with advanced analytics, artificial intelligence, and machine learning techniques. These tools address the evolving landscape of cybersecurity challenges by boosting threat detection capabilities, improving response times, and maintaining a proactive approach to cybersecurity.
We will invest when we develop and refine our algorithms, maintain training programs to IT teams to leverage the technology, upgrade the digital infrastructures to support interoperability, and stay informed of best practices to incorporate into our strategy.
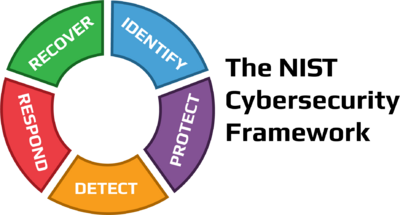
The Swoosh Chart above captures the initial stage of CSM technology to offer continuous security monitoring for endpoints. The next point highlights the rapid growth phase, where AI and ML are integrated into the technology to optimize performance and offer near-real time detection and mitigation. In the stabilization phase, the technology is able to have the intelligence to have prediction capabilities. The evolution of the technology follows the NIST Cybersecurity Framework's pillars to detect, respond, and recover, and the technology has the future ability to predict, automating the remaining pillars identify and protect. The automation of the technology will allow prevention mechanisms that no human has thought of before.
References
[1] Google Patents. 2018. Network asset continuous safety monitoring method, system, equipment and storage medium. Retrieved from [1]
[2] Google Patents. 2017. Information security network integrated management system using big data and artificial intelligence, and a method thereof. Retrieved from [2]
[3] Google Patents. 2017. A kind of network security monitoring method towards industrial control system. Retrieved from [3]
[4] IEEE Xplore. 2021. Leveraging Information Security Continuous Monitoring to Enhance Cybersecurity. Retrieved from https://ieeexplore.ieee.org/document/9799002
[5] ACM Digital Library. 2023. APIRO: A Framework for Automated Security Tools API Recommendation. Retrieved from https://dl-acm-org.libproxy.mit.edu/doi/10.1145/3512768
[6] ACM Digital Library. 2010. Monitoring for security intrusion using performance signatures. Retrieved from https://dl-acm-org.libproxy.mit.edu/doi/10.1145/1712605.1712623
[7] OSSEC. 2021. Getting started with OSSEC. Retrieved from https://www.ossec.net/docs/docs/manual/non-technical-overview.html
[8] Wazuh. 2023. The open source security platform. Retrieved from https://wazuh.com/
[9] Gartner. 2023. Elastic Security Reviews. Retrieved from https://www.gartner.com/reviews/market/endpoint-protection-platforms/vendor/elasticsearch/product/elastic-security
[10] Splunk. 2023. Splunk Enterprise Security. Retrieved from https://www.splunk.com/en_us/products/enterprise-security.html
[11] Rapid 7. 2023. Security information and event management. Retrieved from https://www.rapid7.com/products/insightidr/features/security-information-event-management/
[12]Crowdstrike. 2023. Falcon: The world’s leading AI-native platform for unified next-gen antivirus. Retrieved from https://www.crowdstrike.com/products/endpoint-security/falcon-prevent-antivirus/
[13] Cybersecurity Ventures. 2020. History of hacking and defenses. Retrieved from https://cybersecurityventures.com/the-history-of-cybercrime-and-cybersecurity-1940-2020/
[14] Statista. 2023. Median time from compromise to discovery in days of larger organizations worldwide from 2014 to 2019. Retrieved from https://www.statista.com/statistics/221406/time-between-initial-compromise-and-discovery-of-larger-organizations/
[15] Gartner. 2023. List of Critical Capabilities for Cloud Access Security Brokers. Retrieved from https://www.gartner.com/document/4366499
[16] Oberheide, J., & Cooke, E. 2008. CloudAV: N-Version Antivirus in the Network Cloud. Retrieved from https://www.semanticscholar.org/paper/CloudAV%3A-N-Version-Antivirus-in-the-Network-Cloud-Oberheide-Cooke/1ca0b25bd4fe4994f7f5e334987588776a1a123c
[17] Secureworks. 2017. The Evolution of Intrusion Detection & Prevention. Retrieved from https://www.secureworks.com/blog/the-evolution-of-intrusion-detection-prevention
[18] ISACA. 2021. The Evolution of Security Operations and Strategies for Building an Effective SOC. ISACA Journal, 5. Retrieved from https://www.isaca.org/resources/isaca-journal/issues/2021/volume-5/the-evolution-of-security-operations-and-strategies-for-building-an-effective-soc
[19] Pure Storage. 2023. What is SOAR? Retrieved from https://www.purestorage.com/knowledge/what-is-soar.html
[20] Brand Essence Research. 2023. Security Orchestration, Automation and Response Market. Retrieved from https://brandessenceresearch.com/security/security-orchestration-automation-and-response-market
[21] CrowdStrike. 2023. Falcon Insight XDR. Retrieved from https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/
[22] CrowdStrike. 2023. CrowdStrike Announces General Availability of Falcon XDR. Retrieved from https://www.crowdstrike.com/press-releases/crowdstrike-announces-general-availability-of-falcon-xdr/
[23] National Institute of Standards and Technology. 2023. Cybersecurity Framework. Retrieved from https://www.nist.gov/cyberframework