Difference between revisions of "Healthcare Data Security"
BruceHecht (talk | contribs) |
BruceHecht (talk | contribs) |
||
| Line 202: | Line 202: | ||
| 4|| % of devices that are IOMT || Networked or smart devices (Internet of Medical Things) || 48%-68% | | 4|| % of devices that are IOMT || Networked or smart devices (Internet of Medical Things) || 48%-68% | ||
(increasing over study period) || Market requirements | (increasing over study period) || Market requirements | ||
|- | |||
| 5 || Market capture || Percent of IoMT devices served by Penultimate Frontier products || 5%-50% || | | 5 || Market capture || Percent of IoMT devices served by Penultimate Frontier products || 5%-50% || | ||
|- | |||
| 6 || Revenue/device || Pricing ASP (Average Sales Price) per unit || $20 || | | 6 || Revenue/device || Pricing ASP (Average Sales Price) per unit || $20 || | ||
|- | |||
| 7 || Cost as % revenue (device revenue) || Cost as % revenue, with declining cost over study period || 30%-17% || Compute Resource | | 7 || Cost as % revenue (device revenue) || Cost as % revenue, with declining cost over study period || 30%-17% || Compute Resource | ||
|- | |||
| 8 || Deployment cost/device || Deployment cost (average) for each unit | | 8 || Deployment cost/device || Deployment cost (average) for each unit | ||
(non-recurring) || $1 || | (non-recurring) || $1 || | ||
|- | |||
| 9 || Discount rate || Discount rate used in evaluating Net Present Value (NPV) to represent opportunity cost and time value of revenues vs investments || 10% || | | 9 || Discount rate || Discount rate used in evaluating Net Present Value (NPV) to represent opportunity cost and time value of revenues vs investments || 10% || | ||
|- | |||
| 10 || R&D investment || Proposed budget for R&D projects || $50M || | | 10 || R&D investment || Proposed budget for R&D projects || $50M || | ||
|} | |} | ||
Revision as of 22:04, 18 November 2020
Healthcare Data Security Technology Roadmap
- 2HDS Healthcare Data Security
Roadmap Overview
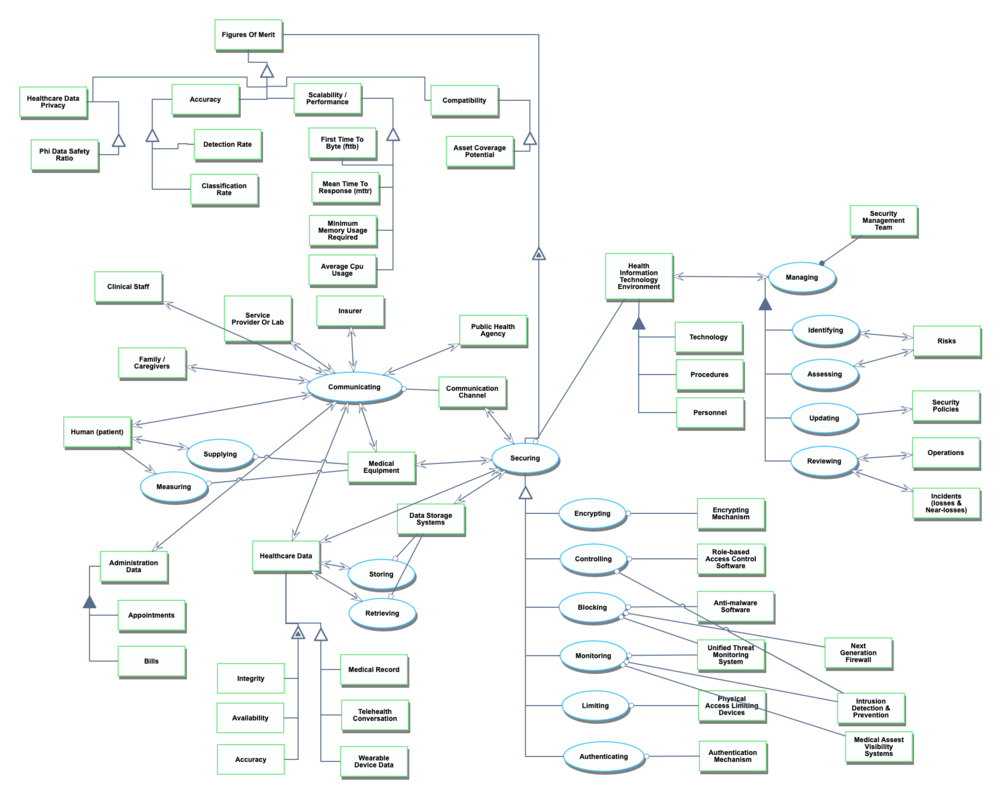
The context, working principles, and architecture for healthcare data security is shown in the following diagram. Note the presence of a threat actor potentially compromising security and whose interference the healthcare data security technology is intended to deter, prevent, detect, and/or mitigate.
Health is an essential aspect of life, connected to each individual and to families and our societies, as well as forming an integrated element of the economy. Distributing healthcare to the point of care may improve outcomes, reduce risks, and reduce costs. Patients, healthcare workers, and healthcare organizations require trust in the security of these systems in order to adopt the systems and to avoid losses. Regulation is primarily made at the national level and requires that health privacy and security are effectively achieved. Compliance to HIPAA requirements apply in the United States<ref name="HIPAA">CDC.gov HIPAA description,“Health Insurance Portability and Accountability Act of 1996 (HIPAA) | CDC.”</ref> , and the EU General Data Protection Regulation (GDPR) applies to operations within EU countries, to data about EU residents, and to any organization that interacts with data of citizens of EU countries.<ref name="GDPR">THE EUROPEAN PARLIAMENT AND THE COUNCIL OF THE EUROPEAN UNION, General Data Protection Regulations (GDPR), 2016.</ref> Healthcare coordination and efficiency may be improved through the use of electronic medical records / electronic health records (EMR / EHR) which may be maintained using on-premises or by using cloud computing services. Over the past decade, increased adoption has focused an attention on the need for systems and technologies to provide for security and privacy while maintaining efficiency and scalability.<ref name="Colicchio_2019">T. K. Colicchio, J. J. Cimino, and G. Del Fiol, “Unintended consequences of nationwide electronic health record adoption: Challenges and opportunities in the post-meaningful use era,” Journal of Medical Internet Research, vol. 21, no. 6. Journal of Medical Internet Research, p. e13313, Jun. 01, 2019, doi: 10.2196/13313.</ref><ref name=Al-Issa_2019>Y. Al-Issa, M. A. Ottom, and A. Tamrawi, “Review Article eHealth Cloud Security Challenges: A Survey”, 2019, doi: 10.1155/2019/7516035.</ref>
This roadmap study focuses on the topic of securing healthcare data, with an emphasis on the virtual world over the physical world, which is largely descoped aside from the stakeholders within the ecosystem for the purposes of this project. The overall objective is to main maintain privacy and safety for patients participating in the healthcare system. Specifically, the technology includes the various tools and methods that allow for the secure transmission, storage and retrieval of healthcare data, with an emphasis on “communication” within a virtual healthcare environment. This includes security controls such as encryption or ransomware prevention capabilities. The roadmap includes security measures aimed to mitigate risk associated with 1) malicious threat actors, purposefully attempting to collect data that these individuals should not have access to, as well as 2) accidental data disclosure, with no malicious intent behind the occurrence. The surface area of assets includes telehealth appoints, wearable devices and medical records.
Design Structure Matrix Allocation
The Healthcare Data Security (2HDS) tree that is extracted from the Design Structure Matrix (DSM) above shows that the Healthcare Data Security (2HDS) is in the context of a larger Healthcare Living System (1HLS) and requires the subsystems of Security Software Systems (3SECSW), Security Physical Systems (3SECPHYS), Physical Data Systems (3PDS). The Security Software Systems (3SECSW) and Security Physical System (3SECPHYS) in turn requires several enabling Layer 4 technologies: Encryption Mechanism (4ENCRM), Role-Based Access Control Software (4RBACSW), Anti-Malware Software (4AMSW), Unified Threat Management System (4UTMS), Least Privileged Access Systems (4LPAS), Authentication Mechanism (4AM). The Physical Data System (3PDS) requires in turn the enabling Layer 4 technologies of: Data Storage System (4DSS) and Communication Channel (4COM).
Roadmap Model Using OPM
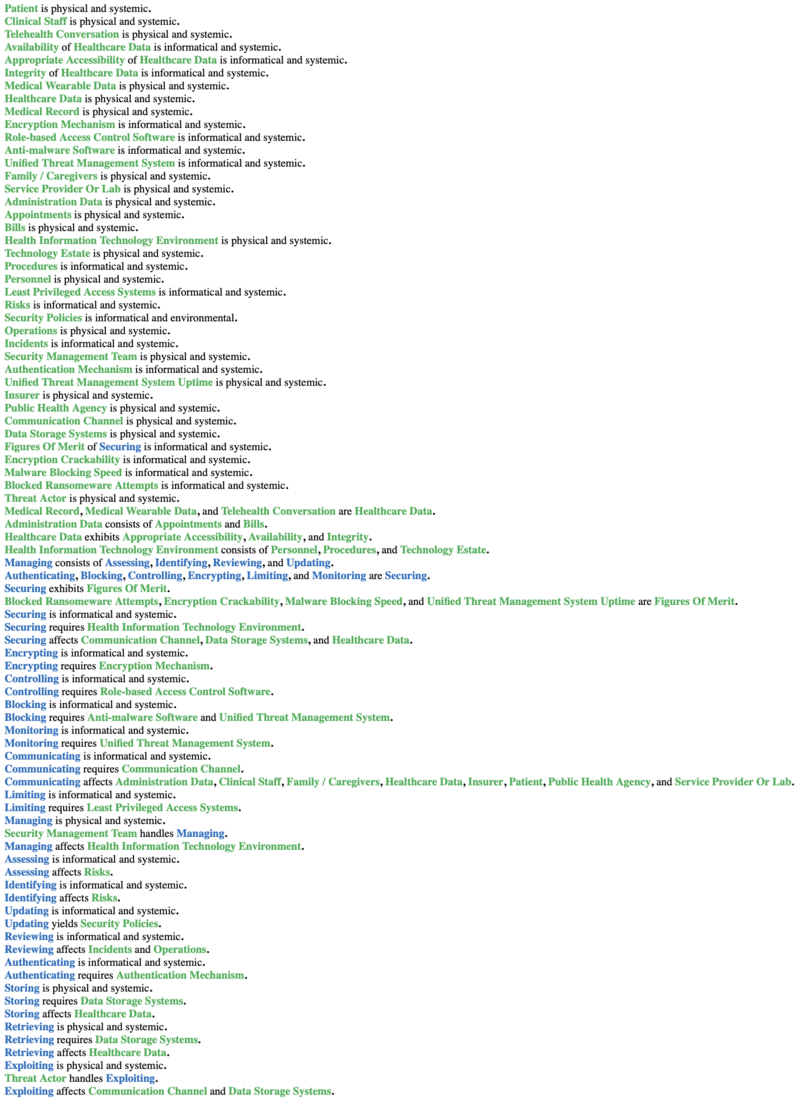
An OPM model is provided here for the 2HDS roadmap in the figure below. This diagram captures the main object of the roadmap (Healthcare Data Security), its decomposition into subsystems (Human Actors, Data Storage Systems, Communication Processes that interact with the Communication Channel, Securing Processes that interact with the Health Information Technology Environment, Health Organizations including Insurer, Service Provider or Lab, Public Health Agency, and Family/Caregivers), its characterization by Figures of Merit (FOMs) as well as the main processes (Communicating, Storing, Retrieving, Securing, and Managing). The potential Threat Actor is identified with the potential for the damaging process of Exploiting vulnerabilities in the elements of the system.
An Object-Process-Language (OPL) description of the roadmap scope is auto-generated by the OPCLOUD software and is given below. It reflects the same content as the previous figure, in a formal natural language.
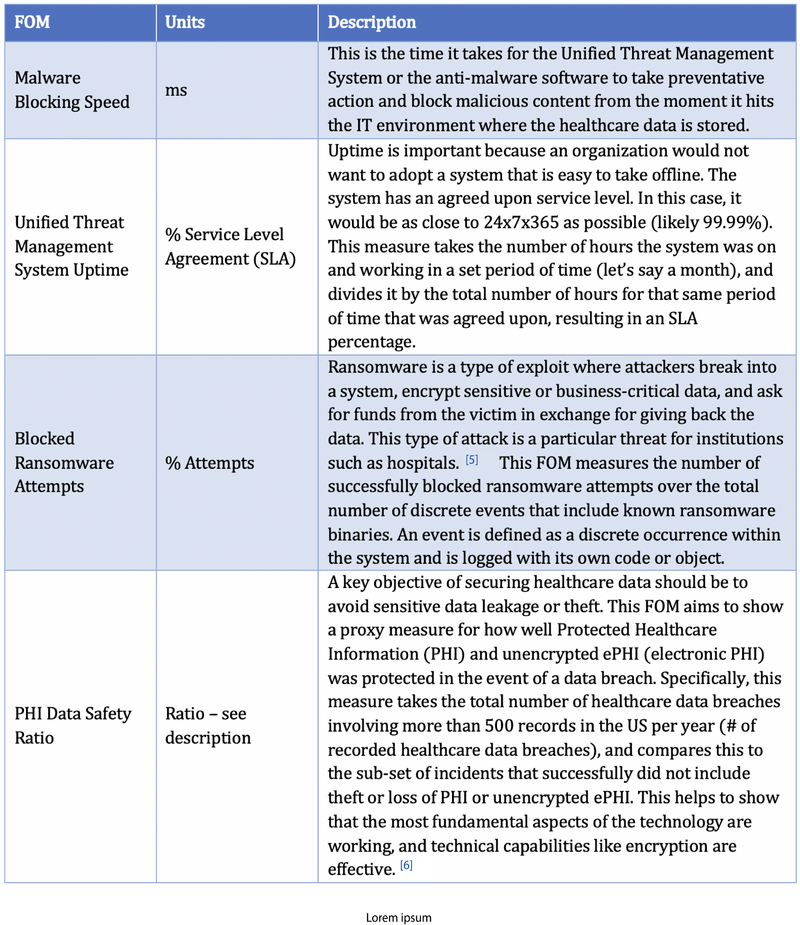
Figures of Merit
Health Data Security Figures of Merit (FOM) are described in the following table.
References<ref name="whatis">kaspersky.com, "What is Ransomware?", June 11, 2020.</ref>
<ref name=HIPAAJournal>"Healthcare Data Breach Statistics," HIPAA Journal.
</ref>
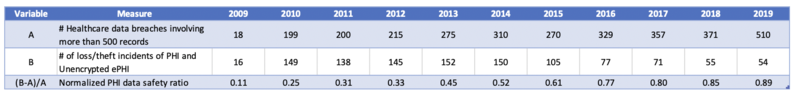
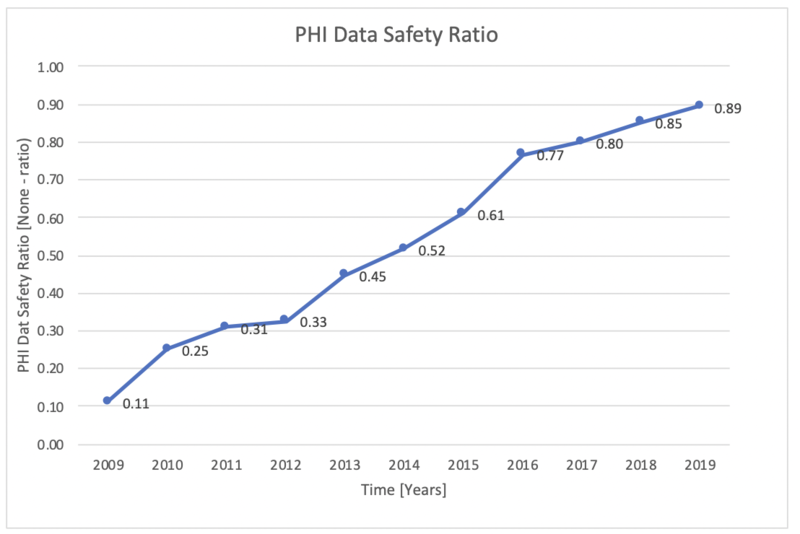
Publicly available data collected by the Office of Civil Rights (OCR) helped the team to create a meaningful PHI Data Safety Ratio as a FOM. The data available includes the total number of discrete healthcare data breaches that involve more than 500 healthcare records from 2009-2019. As a subset of this data, the OCR recorded the number of loss or theft incidents that included PHI or unencrypted ePHI.<ref name="whatis" /> We took the delta between these two data sets to look at the number of incidents that did not include PHI (or unencrypted ePHI), using this as a proxy for safety. This allows the team to plot a lack of sensitive data loss and therefore a success of healthcare data security implementations between 0 and 1 inclusive, with 1 (i.e., no incidents with PHI or unencrypted ePHI) as the default utopia point.
Patent & Publication Analysis
1. Packet analysis based IoT management [tk]
- Type: Patent (Patent # 10212178; US10771491B2)
- Owner: Palo Alto Networks (Inc.) for their medical device security product offering under ZingBox, Inc.
- Key dates: Filed on February 2019 and application granted September 2020
- Description: This technology is allowing for network packets to be analyzed when going to or from an Internet of Things (IoT) device in the context of preventing attacks against these devices. Through this technology, uncharacteristic behavior deriving from an IoT device can be detected using historical data from the device itself that is collected over time. Packet data can both be inspected and triangulated with what is considered standard behavior based on previously collected event logs and IoT device characteristics, ultimately generating in anomaly detection notification.
- Applicability to roadmap: Zingbox is a major player in the expanding Internet of Medical Things (IoMT) security industry [4]. Our focus on medical device security via threat detection and prevention is highly related to this patent; this technology describes a specific example of how anomalies can be detected on IoT devices that are ultimately indicative of cyber-attacks. It builds upon well-established technologies from the security space (packet capture, event logging, vulnerability identification) and combines this technical capabilities to form a new methodology that may be better suited for identifying anomalous behavior in IoT by crafting device profiles rather than the ‘one size fits all’ approach IT security tools (although the team has not seen implementation data that would demonstrate higher rates of accurate detection or better infrastructure compatibility – this is the assumed benefit/FOM area).
2. Systems and methods for detecting a cyberattack on a device on a computer network [tk]
- Key dates: Provisional application filed on December 2017 and July 2018; publication occurred on June 2019, with the patent still pending
- Owner: Mercy Health
- Description: The technology focuses on detection in the context of a cybersecurity attack, as applicable to medical devices. Data is collected through a honeypot scheme, where attackers are geared towards dummy medical devices set up within the same IP subnet as actual medical devices. This allows for the collection of attack techniques from actual threat actors, which in turn generate Indicators of Compromise (e.g., types of obfuscation techniques, multiple failed attempts to access a device within a set timeframe) that serve as the basis for malicious event detection alerts.
- Applicability to roadmap: This technology relies on medical devices as the dummy infrastructure, and is specific to detection in the context of cybersecurity attacks – this is squarely aligns with medical device cyber threat prevention and detection. This newer incorporation of OT into the targeted assets makes it difficult for existing security products (firewalls, anti-virus, etc.) to effectively detect attacks meant specifically for medical devices rather than IT. The technology scheme relies on the collection of data from real attacks actually occurring on the network to enhance medical device security detection. The team interpreted a baked-in assumption that the risk of setting up a honeypot is outweighed by the benefits of collecting highly applicable and accurate data on threat actor threat techniques (As an aside, this was a very fun technology to discovery – it’s a great idea if the benefits outweigh the risks).
3. Fernandez Maimó et al., “Intelligent and Dynamic Ransomware Spread Detection and Mitigation in Integrated Clinical Environments.” [tk]
- Publication Date: 5 March 2019
- Authors: Lorenzo Fernández Maimó, Alberto Huertas Celdrán, Ángel L. Perales Gómez, Félix J. García Clemente, James Weimer, and Insup Lee
- Publication Name and Details: “Intelligent and Dynamic Ransomware Spread Detection and Mitigation in Integrated Clinical Environments.” Sensors 19, no. 5 (2019): 1114.
- doi:10.3390/s19051114
- Applicability to roadmap: This paper describes cybersecurity requirements and vulnerabilities for Medical Cyber-Physical Systems (MCPS). Consideration of ransomware attacks as the leading type of attack is reported as 85% of cases, with 70% of attacks involving confirmed data loss. The paper reviews potential technology to address these concerns. The focus is on automating detection of attacks through machine learning (ML) and real-time operations.
4. Markus Willing et al., “Analyzing Medical Device Connectivity and Its Effect on Cyber Security in German Hospitals.” [tk]
- Publication Date: 29 September 2020
- Authors: Willing, Markus, Christian Dresen, Uwe Haverkamp, and Sebastian Schinzel.
- Publication Name and Details: “Analyzing Medical Device Connectivity and Its Effect on Cyber Security in German Hospitals.” BMC Medical Informatics and Decision Making 20, no. 1 (September 29, 2020): 246.
- doi: 10.1186/s12911-020-01259-y
- Applicability to roadmap: This paper explores the use of networked devices in hospitals and the risks for cyber attacks. The authors analyze networked medical devices in German hospitals by considering the departments with largest use of devices and their vulnerabilities. In this recent study published this September, the authors report 5000-40000 active medical devices per hospital with an increasing percentage that are networked devices. The largest increases are reported in the departments of Radiology, Intensive Care, Radio-Oncology, and Nuclear Medicine.
Strategic Drivers
Company vs. Competition
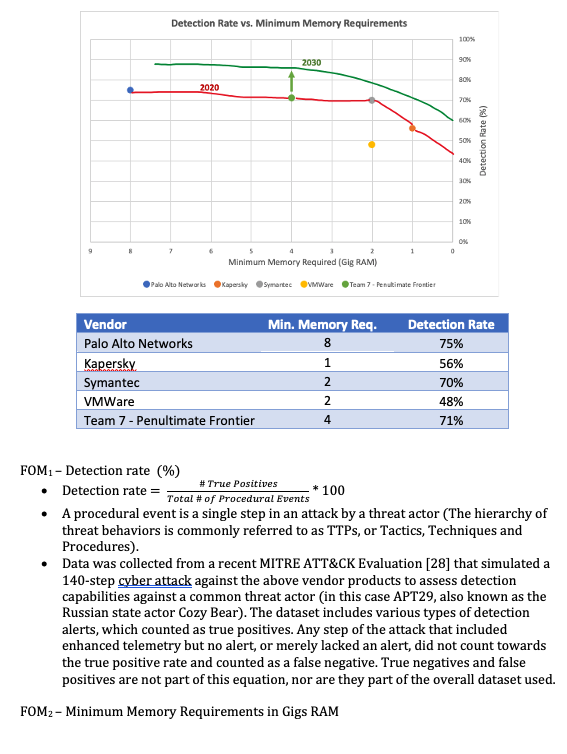
Security for the Internet of Medical Things (IoMT) is a relatively new industry with data often kept confidential. Key players in the medical device security space include companies such as CyberMDX, Medigate, Armis (acquired by Insight Partners), and Palo Alto Networks [35][36][37]. These vendors have not subjected their tools to broad public assessments yet, nor are the underlying detection algorithms associated with each known. As a proxy, the team selected vendors that were either a) also a player in the Medical or general IoT space, or b) has integrations with the medical device detection vendor tools. Minimum required Gig serves as a measure of minimum resource usage (processor requirements were not consistent enough to use), with fewer RAM usage preferred.
Based on where the Penultimate Frontier sits in this space today, the company strategy would be to improve accuracy at the expense of required RAM usage if investment dollars were a constraint. This is because Palo Alto Networks, which is even further to the left of the Penultimate Frontier, is considered a successful player in the space [35], and the resource requirements do not serve as a significant deterrent at this time. Detection rate is a key FOM within the industry and studied in academia, and therefore the firm should prioritize improving this capability as much as possible.
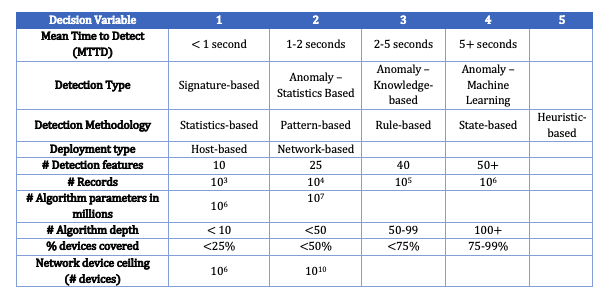
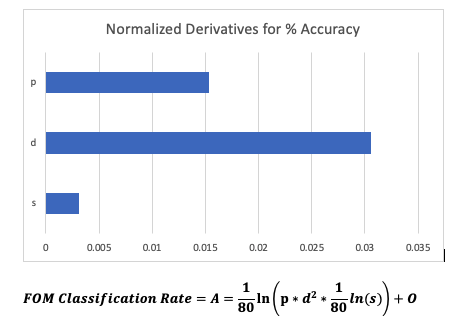
Technical Model: Morphological Matrix and Tradespace
- p = # of algorithm parameters in millions
- d = # of algorithm depth (layers)
- s = percent of estate visible to detection algorithm
- c complexity = p*d^2
- O = constant to interpret solution as a percentage
- Classification Rate (e.g., Accuracy) A = (true positives + true negatives)/ all events
Morphological Matrix
Key FOM
Financial Model and R&D Projects
[ Note – Please ignore earlier sections, we are working to adjust what was covered in earlier sections of the roadmap -- particularly the FOMs]
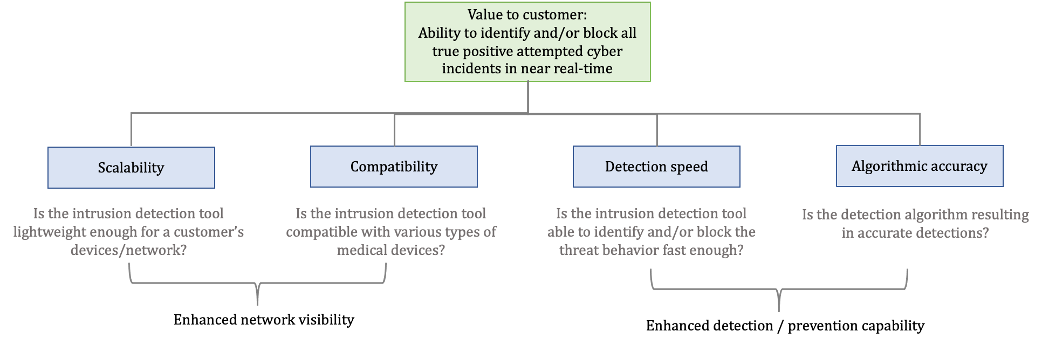
The overall value to a customer to properly secure an Internet of Medical Things (IoMT) device against attacks is to be able to identify and prevent a cyber attack from exploiting the device. While there are several mechanisms to do this (e.g., encryption, vulnerability management, different segregation for network deployments), the value of a distinct intrusion detection and/or prevention solution, at its core, can be summarized here as the ability to detect a true positive cyber attack in near real-time. False positives, while a nuisance to the customer due to potential business disruption, are far less of a risk than a false negative – i.e., behavior on the network or device that is misidentified as benign. Therefore, while ease of use is a factor for why a customer would value a product, it is a secondary consideration.
The drivers of this value to the customer can be broken down in the following ways:
| # | Category | R&D Investment/Tech Infusion | Rationale | Key Dependencies | Target Impact Goal |
|---|---|---|---|---|---|
| 1 | Network Visibility | Hybrid host and network, cloud-based solution (Network Intrusion Detection System for IoMT) | Improved scalability; increasing attack surface | Time and resources to adjust tool architecture | 20% decrease in throughput speed (gbs/sec) given existing load balancing |
| 2 | Network Visibility | Device protocol security inclusion (POCT01, LIS02, DICOM, proprietary) | Improved coverage; increasing attack surface; highly vulnerable protocols | Ability to work with vendors (GE, Philips) to understand proprietary protocols | 10% increase in coverage potential (average % of IoMT devices compatible with tool /hospital) |
| 3 | Detection/prevention capability | Machine Learning-based detection | Greater algorithmic accuracy, particularly for detecting new types of threat techniques | Algorithm training time, data set availability, compute resources | 5% increase in accuracy |
| 4 | Detection/prevention capability | Incorporation of FPGA (Field-Programmable Gate Array) hardware | Increased detection speed; low bandwidth and energy usage | High engineering costs | 10% increase in detection speed |
A key component of the financial model is the projected increase in market demand based on the threat landscape. The attack surface of hospitals will increase by at least 20% within a 5 year period, with expected continual growth. The attack surface increase is driven by moving offline medical devices online, or upgrading from older devices to IoMT. At the same time, the increasing attack surface area and a history of successful exploits will drive up the number of attacks on hospitals. From 2019 to 2020, ransomeware attacks were expected to quadruple – COVID-19 and the election have altered these estimates, with hospitals experiencing up to a 75% uptick in ransomware attacks since Q1 2020. These trajectories, as well as the other assumptions outlined informed our Monte Carlo Simulation of the Financial Model.
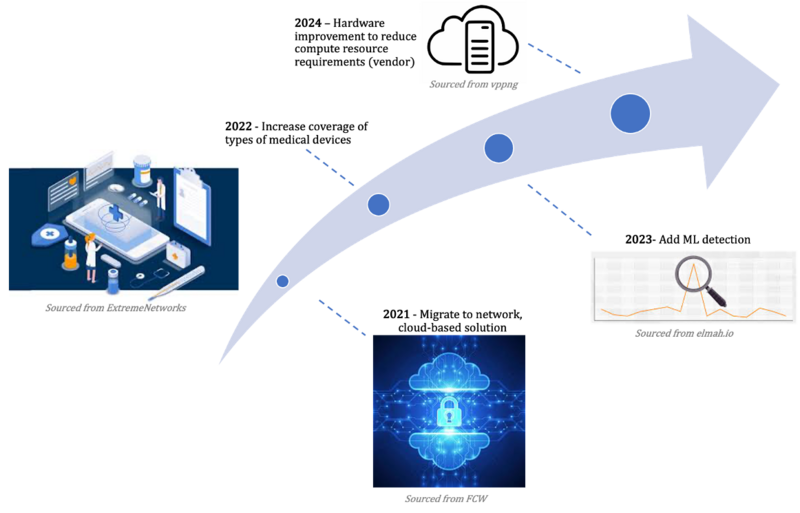
R&D Project Option #1: Shift from host-based solution à Hybrid host and network, cloud-based solution
Improving scalability: Currently, The Penultimate Frontier’s intrusion detection solution is host-based, meaning this is an agent-based deployment (i.e., on each endpoint, either a medical device or the connected server). This makes it difficult to scale across networks that are increasingly putting medical devices online, especially given compute constraints and issues with latency described in previous sections. In 2020 alone, more than 250 million devices shipped to medical providers [CyberMDX]. The aim would be to move to a cloud-based solution with a more centralized architecture to account for an increase in network visibility coverage needs by medical providers.
Impact:
R&D Project #2 – + Increase coverage of device binding ports / protocols specific to medical devices Improving coverage: A customer, such as a hospital, may want to cover and even deploy intrusion detection solutions across their technology estate, but the efficacy of this effort is reliant on the uniqueness of the various types of medical device first coming online. Even if one device, say an MRI machine, in this hypothetical was kept perfectly secure via an intrusion detection tool, if all of the CT scan machines are connected to the network and not compatible with the existing solution, the hospital will either 1) purchase another solution or, more likely 2) keep the CT scan machines online and exposed. Increasing the protocol coverage type for intrusion detection capabilities would enable a larger percentage of a hospital’s online device to be protected. Note that there are two standards that exist today for the interoperability of medical device connectivity – namely, CEN ISO/IEEE 11073. However, many hospital devices use outdated or insecure protocols. While updated this should be the responsibility of the IT stakeholders within a hospital, a good detection tool would be driven off of the reality that these vulnerable areas will exist within a hospital’s network and require enhanced detection. Some device protocols are also proprietary, so either a one-size-fits-all solution or collaboration with those vendors (GE, Philips etc.) would be necessary.
Tech infusion impact: Decrease compute
R&D Project Option #3 – + Add Machine Learning detection to existing signature and anomaly-based detection methodology
R&D Project Option #4 – + Incorporation of FPGA hardware
The financial model we are exploring relates to the investments made for cybersecurity in support of networked medical devices. These are sometime referred to as the “Internet of Medical Things” (IOMT).
A set of 4 technology areas relate to the product and service for Penultimate Frontier’s cybersuite.
3 areas relate to the technology applied to the individual medical devices that are at risk for patient care in hospital settings. One additional technology area is the technology for compute resources needed as the infrastructure to support the deployment of the cybersuite capability at the hospital.
| # | Technology Area | Type | Description | Notes for R&D Investments |
|---|---|---|---|---|
| 1 | Scalability | Product technology | Intrusion detection | Move from agent-based to cloud-based |
| 2 | Device Coverage | Product technology | Coverage of device binding ports / protocols | Increase protocol coverage |
| 3 | Detection Algorithms | Product technology | Algorithms to detect activity and identify accurately | Extend machine learning methods for adaptive response |
| 4 | Compute Resources | Deployment infrastructure | Deployment to newly added medical devices incurs a cost for setup | Automation for reducing cost of setup |
| # | Model element or parameter | Description | Value | R&D Project Target(s) |
|---|---|---|---|---|
| 1 | Large hospitals (USA) | Number of large hospitals, USA | 6146 | |
| 2 | Forecast range | Years | 2020-2025 | Target timeframe |
| 3 | Devices/hospital | Number of medical devices per hospital (total) | 7500 | Current group served |
| 4 | % of devices that are IOMT | Networked or smart devices (Internet of Medical Things) | 48%-68%
(increasing over study period) || Market requirements | |
| 5 | Market capture | Percent of IoMT devices served by Penultimate Frontier products | 5%-50% | |
| 6 | Revenue/device | Pricing ASP (Average Sales Price) per unit | $20 | |
| 7 | Cost as % revenue (device revenue) | Cost as % revenue, with declining cost over study period | 30%-17% | Compute Resource |
| 8 | Deployment cost/device | Deployment cost (average) for each unit
(non-recurring) || $1 || | ||
| 9 | Discount rate | Discount rate used in evaluating Net Present Value (NPV) to represent opportunity cost and time value of revenues vs investments | 10% | |
| 10 | R&D investment | Proposed budget for R&D projects | $50M |
Technology Strategy Statement
tktk
HI