Difference between revisions of "Continuous Security Monitoring"
(Added images and adjusted size) |
(Added verbiage to OPM) |
||
| Line 8: | Line 8: | ||
[[File:Screen Shot 2023-10-12 at 1.05.40 AM.png]] | [[File:Screen Shot 2023-10-12 at 1.05.40 AM.png]] | ||
=== DSM Allocation | === DSM Allocation === | ||
[[File:DSM for Continuous Security Monitoring .png|750x750px]] | [[File:DSM for Continuous Security Monitoring .png|750x750px]] | ||
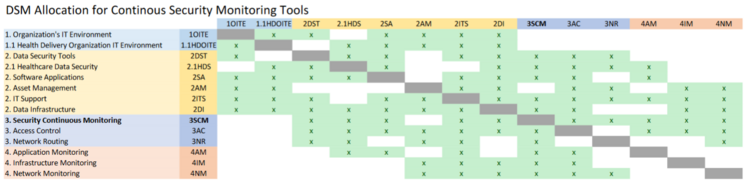
The most inter-dependencies are with the Healthcare Data Security (2HDS) roadmap. | The most inter-dependencies are with the Healthcare Data Security (2HDS) roadmap. The Healthcare Data Security roadmap is narrowed in to a specific industry whereas we are focused on the more generalized industrial application but a deeper technical level of data security, Continuous Security Monitoring. The higher levels are essentially the same across roadmaps, but industry specific vs generalized. As such, we’ve marked the Healthcare specific roadmap items as subcategories underneath the non-industry specific version. We decided to omit the industry specific items, such as Medical Device Protection, from our DSM. | ||
[[File:CSM DSM Hierarchy.jpeg|500x500px]] | [[File:CSM DSM Hierarchy.jpeg|500x500px]] | ||
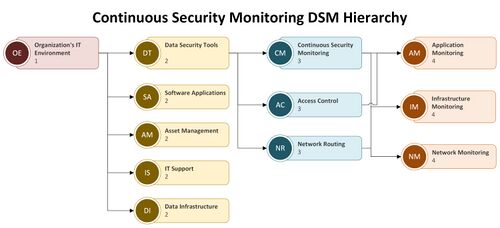
A more detailed view of the levels for the roadmap interactions is provided in hierarchy form. | |||
=== Roadmap Model using OPM (ISO 19450) === | === Roadmap Model using OPM (ISO 19450) === | ||
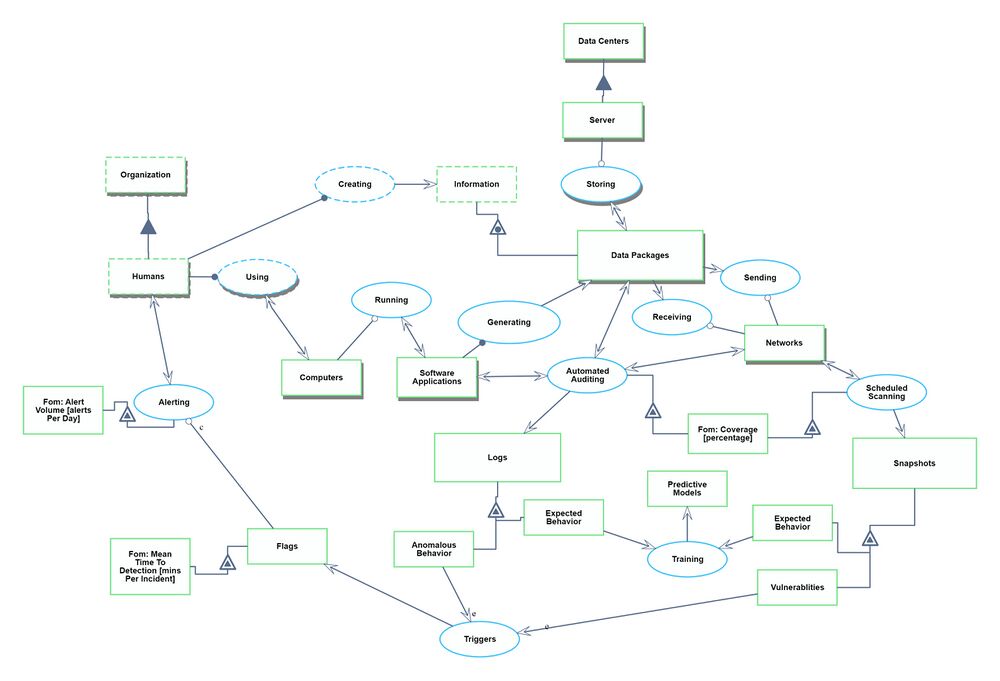
We defined a Continuous Security Monitoring Tool to sit within the environment of an organization's IT infrastructure. The system contains the IT landscape at a high level, such as software applications, data infrastructure, and network routing. We narrowed to just the monitoring and alerting functionality of a CSM tool. There could be additional functionalities within data security such as root cause analysis, remediation, and pro-active repairs, but we have excluded those from our system. | |||
[[File:Continuous Monitoring Tools SD jpeg.jpg|1000x1000px]] | [[File:Continuous Monitoring Tools SD jpeg.jpg|1000x1000px]] | ||
The Object-Process Model above can be written in natural language as follows: | |||
[[File:OPL of 3CSM.png]] | |||
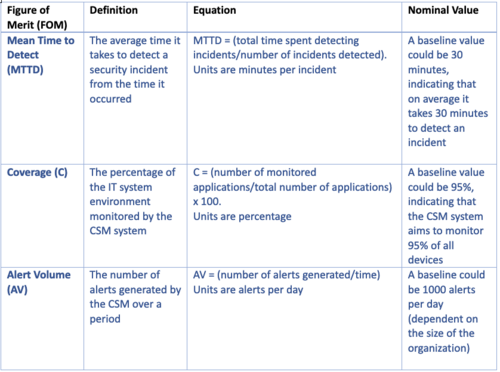
=== Figures of Merit (FOM): Definition (name, unit, trends dFOM/dt) === | === Figures of Merit (FOM): Definition (name, unit, trends dFOM/dt) === | ||
[[File:Screen_Shot_2023-10-12_at_1.15.16_AM.png|500px]] | [[File:Screen_Shot_2023-10-12_at_1.15.16_AM.png|500px]] | ||
Revision as of 07:56, 12 October 2023
Continuous Security Monitoring
Roadmap Overview
A continuous security monitoring (CSM) tool is critical to provide near-real-time surveillance and analysis of an environment to flag potential security threats. The automation of the technology allows ongoing awareness of an environment’s security posture and enhances the ability to manage a potential cybersecurity risk.
DSM Allocation
The most inter-dependencies are with the Healthcare Data Security (2HDS) roadmap. The Healthcare Data Security roadmap is narrowed in to a specific industry whereas we are focused on the more generalized industrial application but a deeper technical level of data security, Continuous Security Monitoring. The higher levels are essentially the same across roadmaps, but industry specific vs generalized. As such, we’ve marked the Healthcare specific roadmap items as subcategories underneath the non-industry specific version. We decided to omit the industry specific items, such as Medical Device Protection, from our DSM.
A more detailed view of the levels for the roadmap interactions is provided in hierarchy form.
Roadmap Model using OPM (ISO 19450)
We defined a Continuous Security Monitoring Tool to sit within the environment of an organization's IT infrastructure. The system contains the IT landscape at a high level, such as software applications, data infrastructure, and network routing. We narrowed to just the monitoring and alerting functionality of a CSM tool. There could be additional functionalities within data security such as root cause analysis, remediation, and pro-active repairs, but we have excluded those from our system.
The Object-Process Model above can be written in natural language as follows: